If you ever kept important files on a USB drive, then you certainly thought about the prospect of misplacing that flash disk and exposing the contents of those files to unwanted people. Even when sending data over the Internet, no one can guarantee that they won't be hijacked during the passage from server to client. Truecrypt is an application that can add an extra layer or two of security to your data storage. It allows you to create encrypted containers that appear to be simple files filled with random data, scramble partitions or whole disks and even protect your operating system by installing it onto an encrypted partition.
It's well known that encryption is a computationally intensive process, so you might think that using it for your day-to-day file operations will only slow you down. It's not so bad if you're using Truecrypt, because its encryption functions are pipelined, parallelized and heavily optimized, so the impact they have on your system's resources is minimal. Also, since the desktop computers nowadays have multiple-gigahertz processors and plenty of memory, the performance penalty induced by the use of encryption is almost unnoticeable.
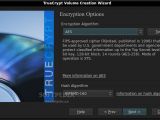
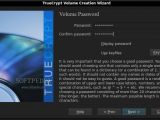
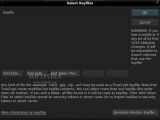
Another nice feature of Truecrypt is its extensive support of encryption algorithms. You get to choose from AES-256, Serpent, or Twofish, and, if you think that neither of those is enough by itself, you can also chain them, but, by doing so, you will have to take into account the noticeable performance penalty. Also, if you feel that your password isn't secure enough, you can strengthen it by using a keyfile, which might be your favorite song or a photo. You just have to remember that you must not modify the file if you want to maintain access to your encrypted container, no id3 tag edits or picture resizing, and it would also be a good idea to choose an inconspicuous file. If you went ahead and bought a dedicated, secure-token device, you can use that too.
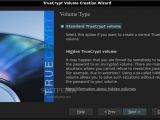
An advanced feature gives you the possibility to create a hidden volume inside another encrypted container, but the complications that arise from choosing this mode of operation make me think that it's only for the more paranoid (or just security conscious) of us. It basically allows you to create an encrypted container in which you're supposed to put decoy files, and that serves as a cover-up for another volume where the truly sensitive data is stored. That way, if you're forced to hand over the password, you can just divulge that of the decoy volume and no one will be able to prove that some other data is stored there. But, if you're not careful when adding data to either one of those volumes, you might end up corrupting data to the other one.
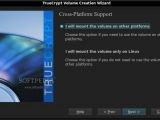
Because it's a multiplatform application, one doesn't need to worry about accessing their data when using different operating systems. Also, the learning curve is quite steep, because Truecrypt's interface is simple enough to allow users to learn about its functions as they use it. Power users aren't left out either, because they can control all of Truecrypt's functions from the command line.
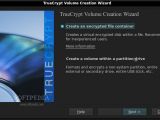
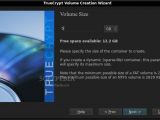
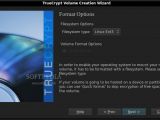
Actually creating an encrypted volume requires the user to go through a simple, step-by-step wizard that has descriptions for every option. Once they get used to it, it takes less than five minutes to create a new volume. If one thinks about the so-called "sparse" volumes that expand to accommodate the files that are added to them, they're out of luck, because such files can only be created on partitions that are formatted using the NTFS file system, which is proprietary to Windows platforms.
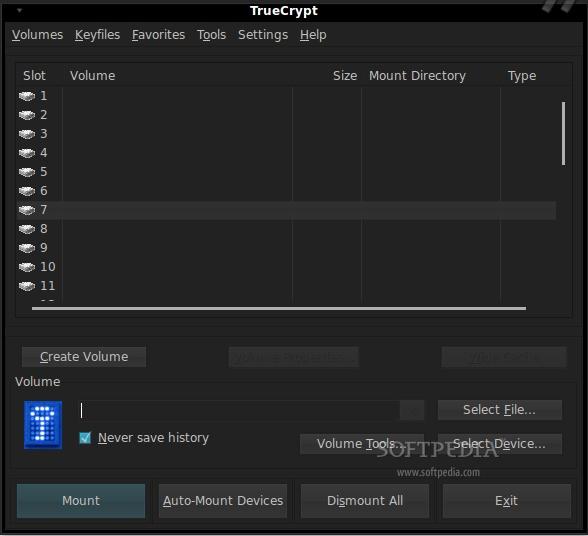
When you're happy with the encrypted volume that you created, accessing it is pretty straightforward. You pick one of the 32 slots in the interface, then you hit the "Select File..." button to load up your volume and press "Mount." You will have to supply your password and keyfiles, then enter your user password to allow TrueCrypt to mount the volume. After that, you will be able to use your encrypted volume just like a normal storage device and copy or move files to it. Don't forget to press "Dismount" when you're done with it.
There are many other Truecrypt options that can make the use of this program more straightforward. If you're unsure about the keyfiles that you want to employ, just look in the "Keyfiles" menu for the function that generates files filled with random content. Also, if you have enough faith that the computer you're using won't be compromised, you can also set default keyfiles that will be loaded automatically when you mount a volume, or even select favorite volumes, saving you of the hassle of browsing the filesystem every time you want to access your encrypted containers.
Unfortunately, system drive encryption isn't possible for Linux-based operating systems. However, there are other ways to achieve full system encryption on Linux, by using Dm-crypt, but that isn't as easy and it often requires changing configuration files by hand.
If you think that Truecrypt looks like a nice piece of software to protect your data, but you want to learn more about it, you will find out that documentation is included in a pdf file, as well as online, and it's well structured and comprehensive. It has screenshots that highlight the discussed functions and quick, step-by-step walkthroughs for the common functions that Truecrypt offers.
 14 DAY TRIAL //
14 DAY TRIAL //