Although (fortunately) I haven’t had my Mac stolen, when I came across Prey, I found it interesting to say the least. The tool really looks like it’s able to catch a thief and, simply because it’s completely free, there’s no reason why this app shouldn’t be running on every Mac out there. And there’s more.
It’s not just that it’s free that makes this tool worthwhile. As with any app, it’s the features that are the selling points. Prey uses a remote activation system, gathers information about your Mac’s location and sends it to your Prey web-based control panel, or directly to your mailbox. Since it sits so silently in your computer, a thief will not be suspicious that his actions are being watched.
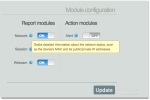
For the sake of the argument, let’s say my Mac got stolen. Luckily, I had installed Prey on it a few days back setting a 2-minute interval between checks, and turning on all report modules, except for the one that alerts the thief I’m watching them. The first thing Prey will do is check if there’s an active internet connection to send the information. If not (and this is the great part), it will attempt to connect to the nearest open Wi-Fi access point available.
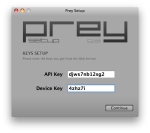
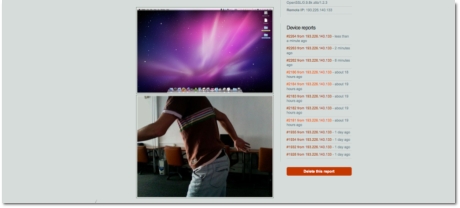
Installing Prey and taking the first simple steps towards configuring the service While using Wi-Fi hotspots, Prey also locates my Mac geographically. Besides gathering information like lat / lng coordinates, it also has an altitude indicator, allowing me to see on which floor of a certain building my computer is. I also get the list of current running programs, the recently modified files, active connections, running uptime and, since my Mac is also iSight-enabled, a snapshot of the person sitting in front of the screen. It may not necessarily be my thief, but, if anything, it may lead me to them. Additionally, keeping up with the latest updates and modules is Prey’s job, so I don’t have to reinstall Prey. The Prey Project team keeps a repository from where Prey will always fetch what it needs.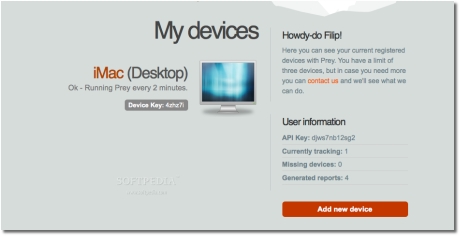
Your device iMac has been marked as missing. Sorry to hear the bad news.
Well, now it the time to keep your eyes open! You can check if new reports arrive at:
http://control.preyproject.com/devices/4zhz7i
Best of luck and hope you can recover your computer. There's always a chance!
-- The Prey Development Team http://preyproject.com
If Prey is able to connect, a different message will be sent to your email account.
Good news Filip!
A new report has arrived for your missing device iMac.
You can check it out at:
http://control.preyproject.com/devices/4zhz7i/reports/2181
Happy hunting!
This is the part where your heart starts pounding in hope of a snapshot of your thief.
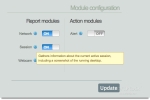
The Prey web control panel is showing me what it was able to fetch - looks like the thief was leaving just now. Bummer! On the downside, as Prey takes a snapshot with the built-in iSight, the green LED turns on. So, if the thief knows anything about Macs (and sees the LED turn on), they’ll most likely become aware of the situation. Then again, the screenshot and picture are sent to me seconds after they’ve been taken, so it’s already too late for my thief.
Important Note While it is always good to have more than one email accounts, it would be wise to use a different email (that isn’t included in your Mail.app’s email accounts) for the Prey reports - you don’t want your thief to see reports before you do.
There’s something else you need to know about Prey. It can work as described today - Prey + Control Panel, or as “Standalone.” Using Prey + Control Panel, you manage your computer’s state and Prey’s configuration through a web page, which also keeps track of all reports sent by Prey from your Mac. It is the most recommended method of use. With Prey Standalone, reports go directly to your inbox but it’s up to you to generate the URL to activate Prey. This way, you don’t need to sign up, but you’ll have to set up the different modules by hand.
The Good
The Bad
The Truth
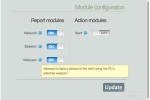
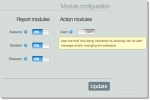
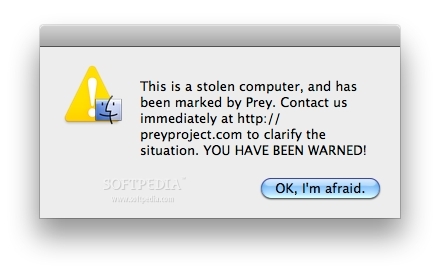
And here’s the alert aimed at spooking your thief (Prey Contol Panel -> Module configuration -> Action Modules -> Alert). Really, does this freak out a thief so bad he’ll actually turn himself in?!
 14 DAY TRIAL //
14 DAY TRIAL //