We're on a roll here at Softpedia when it comes to reviewing antivirus utilities. Yesterday we looked into the brand-new 2015 edition of Bitdefender Internet Security, and two days ago we tested and were pleasantly surprised by Baidu Antivirus 2014.
Today we're shifting our attention to another up-and-coming tool designed for preventing and removing malware, namely 360 Internet Security. Developed by Beijing-based company Qihoo 360, this antivirus solution uses three engines to detect and remove infected or suspicious files. Two of them belong to the developer (360 Cloud, QVM II), while the third belongs to Bitdefender. Just like Baidu, this app is packed in a pleasant and highly intuitive interface. It sports several layers of security made to prevent web-based attacks, in addition to a traces cleaner and sandbox for programs.
NOTE: 360 Internet Security was tested on 64-bit Windows 8.1 Pro.
Installation and interface
The setup procedure is fast and simple, since 360 Internet Security does not ask users to configure any special settings. What's not mentioned, however, is that it automatically integrates an entry into the Windows Explorer context menu, in order to rapidly scan files, folders and drives. Another aspect worth taking into account is that the tool scans the PC for already installed av products, and if found, informs users that they should be removed, in order to avoid any software conflicts most likely to cause OS stability problems.
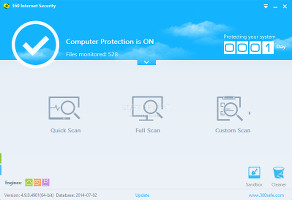
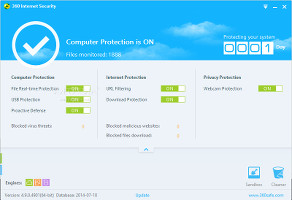
Meet the simple and elegant interface360 Internet Security is wrapped in a user-friendly interface with a pleasant theme and organized layout (hovering the mouse over the Custom Scan button triggers smooth animations). The main menu shows the current PC protection, total files monitored, av engines used, and the app's lifespan, while also providing access to running scans, entering the sandbox and using the traces cleaner.By opening the app's context menu from the system tray icon, it is possible to bring up the main window, configure settings, update the tool with the latest virus definitions, turn off and re-enable real-time protection, as well as enter and exit Do Not Disturb mode.
Different scan modes and configuration settings
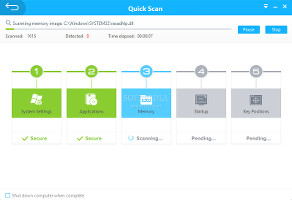
Apart from the previously discussed contextual scan, there are three scan methods available, which are commonly found in most noteworthy av tools. "Quick" focuses on speed and checks only important areas of the computer, namely system settings, applications, the memory, startup entries, and key positions. "Full" does a complete checkup by taking into account the aforementioned locations plus all remaining files. "Custom" scan mode has four predefined options which enable users to quickly evaluate desktop items, My Documents, Microsoft Office documents and CDs. Alternatively, they can handpick the exact drives, directories and files to check. Quick and full scans can be scheduled on a daily, weekly or monthly basis.
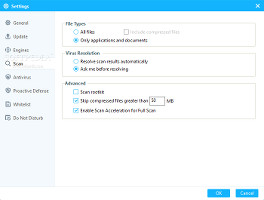
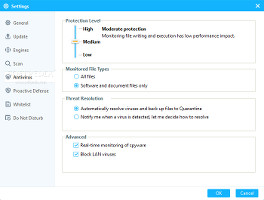
Run a quick scan or configure scan settingsThe default scanning configuration is set to look only for applications and documents, prompt the user for action before resolving threats, skip compressed files larger than 50MB, as well as to enable Scan Acceleration for Full Scan. It is possible to verify all files, include archives and rookits, ask the app to automatically resolve issues, change the minimum size for compressed files to skip or disable it, as well as to disable Scan Acceleration. Any of the three av engines can be disabled.The scanning behavior and steps
During a scan job, 360 Internet Security shows total scanned and detected files along with elapsed time, and it can be set to immediately power off the PC when it finishes. In case of full scans, users may favor either scan speed or resources usage by just clicking a button.
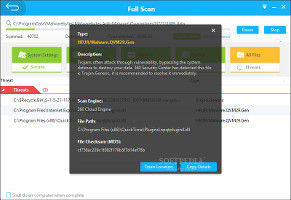
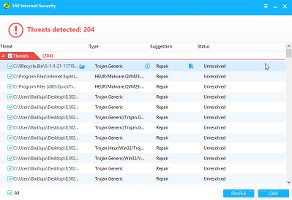
Examine malware names and resolve issuesIf any threats are identified, their full path and type are shown. Users have the possibility to open their location in Windows Explorer as well as to view and copy the malware type's description and MD5 checksum. Infected or suspicious files may be either resolved or trusted by adding them to a whitelist. Final results show total scanned files, threats and deleted files, together with elapsed time. These details and more may be examined in log files.Real-time protection and configuration
By triggering a small button in the main frame, an additional panel appears and shows the current status of the Computer Protection, Internet and Privacy Protection modules. Each component can be deactivated and re-activated with one click: file real-time, download and webcam protection, proactive defense, and USB filtering. Additionally, the tool shows total blocked virus threats, malicious websites and file downloads.
Activate components with one click and configure real-time shield settingsThe three av engines can be selected for the real-time shield separately from the scan engine (by default, the QVM II engine is turned off). It is possible to modify the severity level for continuous protection (monitor file execution, file writing and execution, or all file access) which affects performance impact, keep track of all files instead of software and documents only, ask the app to notify the user on threat detection instead of automatically handling viruses, as well as to disable spyware real-time monitoring and LAN-based virus blocking.Proactive and Self-defense protection, Do Not Disturb profile
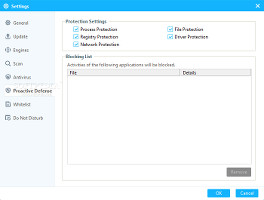
This component ensures the safety of processes, the registry, network, files and drives by monitoring the activity of other programs to identify suspicious patterns and take action before they attempt to damage the computer. Meanwhile, the self-defense module protects 360 Internet Security's own installation and configuration files to prevent any hackers attempting to disarm the PC before infiltrating it (can be disabled).
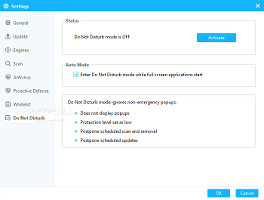
Customize the proactive defense module and enter Do No Disturb mode to turn off alertsThe program's Do Not Disturb profile is basically a gaming profile with optimized settings that can be used when working with other utilities in full screen mode, in order to prevent alert intrusions likely to cause full screen exit, preserve resources consumption by minimizing the av protection level, as well as by postponing any scheduled scans and updates. There are no customization options available here; the profile can be either enabled or disabled.Sandbox and Cleaner
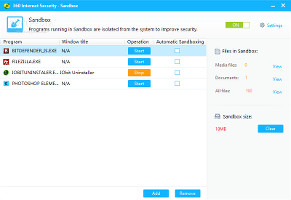
360 Internet Security contains a sandboxing feature that enables users to run any programs in a virtual environment protected by the av utility, in order to prevent any malicious attempts to harm the computer. It can automatically run any apps dropped into the frame and allows users to create exclusions. What's more, it is possible to create an Explorer context menu entry to quickly run files from the sandbox, automatically clear all files and registry entries at system shutdown, and so on.
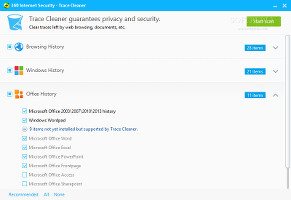
Run apps from the sandbox and remove tracesThe cleaner's purpose it to find and eliminate traces left behind by web browsers, Windows utilities and Microsoft Office products, anything that would compromise user privacy or simply take up space on the disk unnecessarily. It supports Internet Explorer, Mozilla Firefox, Google Chrome, Opera and Safari. All areas covered in each category can be customized before scanning.Quarantine, whitelist, log files, and other settings
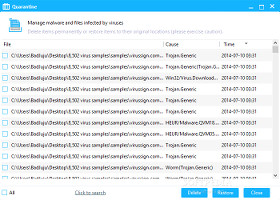
Similar to unveiling the one-click protection module in the main frame, it is possible to display two small frames on the bottom left corner of the primary window to view current CPU and RAM usage, along with total quarantined items. Files sent to the quarantine may be investigated before deciding to delete or restore them to their original location.
Manage the quarantine and examine log detailsFiles and folders sent to the whitelist can be removed, while new ones can be added. Likewise, file extensions may be excluded from the scan jobs and real-time safeguard. From the upper right corner of the screen, users may open the log window to examine statistics on scans, computer and download protection, proactive defense, URL filtering, and software updates.360 Internet Security has several themes available (including one that mimics Bitdefender) and can be removed from the system autostart sequence. It is also possible to remove the Windows Explorer shell extension, disable automatic software updates or set an exact time of day, and so on.
Performance results
We tested 360 Internet Security on an Intel Core i5-3470 @CPU 3.20GHz with 12GB RAM and 500GB Seagate Barracuda ST500DM002 7200RPM, running Windows 8.1 Pro.
We submitted a collection of 8,502 virus samples (no zero-day threats) to find out how many of them are spotted and deleted by the app. Unfortunately, the real-time shield was mostly a disappointment. With default settings applied (medium protection level), the tool was completely unresponsive, even after accessing the files. We had to raise it to high level to see noteworthy response time but it was very slow at removing the files.
However, things started looking up when triggering a contextual scan on the directory in question. As it turns out, 360 Internet Security identified and removed 8,483 files, leaving only 19 files behind. In other words, it had a success rate of 99.7% (which is slightly better than Bitdefender's outcome yesterday).
For the next part of our tests, we ran a full scan with default settings; the entire hard disk had 294GB occupied space. It was completed in outstanding time - 46 minutes and 42 seconds (with Highest Speed enabled, instead of Best Performance). A secondary run on the full scan (we didn't make any modifications to the files in the meantime) was over in just 3 minutes and 22 seconds, since 360 Internet Security resorted to Scan Acceleration Technology to skip unchanged files.
It recorded 2 false positives during the full scan, and detected 5 out of 5 phishing websites.
The Good
During a scanning or removing job, it is possible to explore other interface areas while 360 Internet Security is working in the background.
Scan jobs are extremely fast, and the malware detection ratio was almost perfect in our tests. The program is forgiving when it comes to CPU and RAM consumption during scan jobs (with default settings applied).
The sandbox has plenty of configuration settings to ensure PC safety while confining apps' activity to a secured environment, while the cleaner is fast and effective.
The program is free to use.
360 Internet Security was stable throughout the entire evaluation, unlike many av products.
The Bad
The elapsed time shown is not always accurate (it got stuck in our tests while files were being eliminated).
The "Repair" suggestion made by 360 Internet Security is somewhat misleading, especially if the user is not experienced with av products. The tool does not actually fix the files but deletes them instead.
When detecting some types of viruses, it pops up a full screen alert to prompt users for action and pauses everything else, thus becoming highly intrusive.
The Truth
If the real-time guard was faster and the default configuration was truly optimized, it would've been perfect in terms of performance. 360 Internet Security may seem ideal for beginners, but a bit of tinkering really is necessary to achieve best performance results. Plus, remember to keep an eye out for false positives. Nevertheless, there's always room for improvement. Our overall rating lies somewhere between 4 and 5 stars.
 14 DAY TRIAL //
14 DAY TRIAL //