Zero-day threats. That is what we are all afraid of until the resident antivirus on our computer catches the word and updates. But there are softwares that rely on the behavior of the malware and can spot it from a mile away. This way, by the time the signature for your anti virus software is released, you will already be protected.
Cyberhawk is a free software that can detect malicious processes and prevent their functioning on your computer, without the need of a signature update. This is great news since Z-Day threats are spreading very fast and their morphing would escape the signature provided by the antivirus company. To bring you more good news, Cyberhawk from Novatix is absolutely free. Well, the basic version is, as the full edition will cost you $19.95.
The free version is actually the full edition trimmed down of some of the features. But you can use the full version for 15 days and in case you consider it worthy of your computer it can be purchased for the specified price. The basic version of the software will leave out the Rootkit scanner, Advanced program options, custom rule settings and built-in web search for additional information on threats.
The control panel is easy to use and handle and the tray icon's context menu allows quick suspension of the software's activity on your computer and display of the current monitoring status. Cyberhawk continuously monitors the activity of the processes on your computer and as soon as malicious activity is detected, it will be stopped. This way, you will benefit from 24/7 protection.
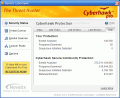
The options running down on the left hand side of the panel window allow you peeks into the Security Status, Threat Control, Rootkit Scanner, Custom Options and program's options. As shown in the Security Status window, the software displays the number of analyzed events, programs examined and the number of detected suspicious activities.
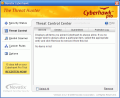
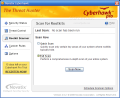
Threat Control window will be empty in the Allowed and Denied categories until the first malicious process is detected and you decide how Cyberhawk should treat it. Rootkits are nasties intended to conceal running processes, files or system data from operating systems. However, the Rootkit Scanner can perform two types of checks on your system. For a fast superficial search there is Quick Scan option which can check only the habitual rootkit hiding places. At the opposite end, there's the Full Scan performing a comprehensive check of the entire system.
The pre-configured security rules Cyberhawk comes equipped with are intended to provide the best protection possible. However, some users may not agree with the developer and wish to add some more rules. The flexibility of the application allows to modify the initial rules and even add some more. The developer warns users that only advanced users should visit the section and they should even manifest care when creating additional custom rules.
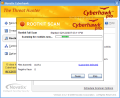
Actually, creating new rules is pretty easy due to the built-in wizard that guides and fully explains the steps. The five items consistent of a rule are source, trigger, options and exclusions. Roughly this means that you will have to select a source from the options available (any process, any non-interactive process, e-mail or browser process or a list of specified processes), choose an event that triggers the rule (accessing a number files - write, execute, create or delete -, renaming files, writing to the registry, creating network connections) and set the options and exceptions when it should be applied.
The final step is giving a name to the rule and providing a short description. I said it was easy as all the above mentioned for creating a rule is translated. My rule resulted in something like: When any process tries to write a file that looks like an executable with a suspicious double extension except when the source process is in the system process list or the source process is in the trusted process list.
The Process list is available in the Custom Rules menu and here you can add all the processes you trust and have no problem with running and also the emails and browsers. If you practically add all the known processes in this list then everything else will be stopped by Cyberhawk and your system will be protected.
The configuration of the application will take place in the Options menu. The three tabs available allows the user to enable Cyberhawk Protection (actively monitors the system for signs of suspicious behavior and potential attacks), Community Protection (by enabling this option you will participate in the Secure Community network of active users that help identify new threats) set a System Restore Point and schedule Rootkit Scanner to check your computer.
As mentioned above, Rootkit Scanner, Custom Rules and Options are features restricted in the full version of the application. So after 15 days of use, no matter how attached you grew of them you will have to let them go or pay the $19.95 fee to bring them back.
The Good
The application is free and offers very good protection against Z-Day threats. There is no option left unexplained due to its help file and the tips scattered in the control panel.
The Bad
After 15 days you will no longer benefit from the Rootkit Scanner, Custom Rules and Options menu. However, the price of the full version is quite appealing.
The Truth
All in all, Cyberhawk is really worth the effort of downloading and installing. Custom Rules option is indeed reserved to experts, but with a little documentation even an average user can do it quite successfully.
Here are some snapshots of the application in action:
 14 DAY TRIAL //
14 DAY TRIAL //