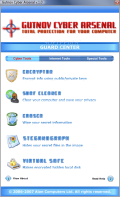
Protecting your personal data and cleaning your traces after a web browsing session is a healthy habit. Keeping your work safe from the hands of the invisible hackers is just as important as protecting it from whoever may gain physical access to your computer. So having a firewall, anti-spyware software and all sorts of safety measures against online attacks is in vain if someone were to handle your computer in your absence. Just as the saying goes "If a hacker gains physical access to your computer, it is no longer your computer", you should shield your machine against any such events.
Cyber Guard offers a series of tools for this matter, such as a file encryptor, a surf cleaner able to eliminate the traces left behind in the web browser, some Windows locations and the recent files in some softwares (Media Player, Paint, WordPad and WinRar). The suite is completed by the Eraser that will secure shredding the sensitive data rendering it unrecoverable. Additional instruments are the Steganograph (hiding secret files in images) and a Virtual Safe to keep your precious files out of reach of prying eyes.
The price for this bunch of tools is $49.95 and the application does a pretty good job. The developer decided to expand the activity area of the program and added more functionality to it by appending additional tools. The name is also changed from CyberGuard to Gutnov Cyber Arsenal. With new tools comes a new price also. And the price tag for this suite is $59.95.
The interface is pretty much the same except for the appended elements and a minor change in the title. There are now three tabs available in the first screen instead of one. The new items added are Internet Tools (comprising a network connections manager, a firewall, a network analyzer and some network utilities) and Special Tools that shelters a system manager, password generator, password saver, an uninstaller and the Invisible Notepad (a tool that creates text documents that can be opened only by it).
I will not go into the CyberTools part as a comprehensive analysis has already been made here and there is no change for this matter. So this leaves us with Internet Tools and Special Tools.
In Internet Tools the first instrument is INet Manager. Unfortunately I could not use it on any of our computers as a nasty error prevented this activity. The iNet utilities are composed of three tools: Ping, Whois and traceroute.
Ping is used to test the availability of a host across the network. The beginner user may feel a little disadvantaged as the ping parameters section is not explained in any way so the values in there may seem encrypted. These values adjust the way the connectivity test is performed. I will try to shed some light on this issue and give you the explanation for all the signs in there.
-T = enabling this will send Echo Request messages to the destination until interrupted. -A = reverse name resolution is performed on the destination IP -f = Echo Request message cannot be fragmented by routers on its way to destination -N = number of Echo Requests sent -l = length in bytes of the Data Field in the Echo Request message -i = the value of the TTL field in the IP header of the Echo Request message -R = records path of the Echo Request and Echo Reply messages -S = Internet Timestamp in the IP header is used to record the Echo Request and Echo Reply messages for each hop
Now these commands are known to an advanced PC user as they are used in ping commands in Windows XP. However, not all the users are aware of their meaning and what they actually do.
Moving onwards to the Whois option which is a little more accessible to the users as it is better known, the options available allow you to choose the Whois server and get going on finding out the desired information. The results will appear quite swiftly, but from now and then there may be a larger delay in displaying the information. The software gives you the possibility of saving the report to a TXT file. This will be sent to the application's installation folder.
Traceroute is somewhat similar to Ping utility as there is no explanation on the parameters offered here either. So here we go again:
-D = not resolving addresses to hostnames (displaying the IP) -H = number of maximum hops to search for destination -W = wait timeout in milliseconds for each reply
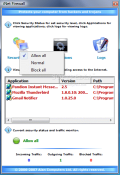
The firewall available in this section is not much and to be frank I do not even know what can be done with it. The Security section has three options: Allow All, Normal and Block All. These are for the applications connecting to the Internet that are displayed in the lower window. The context menu available for each of them enables you to configure for which of them to be alerted, which should be trusted, which should be blocked and which should be terminated immediately.
Proxy checker allows you to load a list of proxies and automatically set them in Internet Explorer. The Settings area for this tool lets you set the timeout for the proxy. Whenever you want to give up to the proxy connection you can simply press the Stop button in the lower part of the screen.
Gutnov Cyber Arsenal comes with a network analyzer designed to scan the network for open ports, hosts, and known trojans. You get to choose the IP range to be scanned or simply perform a scan on the local computer. The verification report includes Open Hosts, Open Ports, Possible Registered Ports and Possible Trojans/Backdoors. The trouble with the last item of the report is that you won't get the location of the malware so that you can root it out.
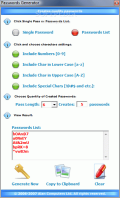
The Special Tools is composed of five instruments almost none of them related to each other. The Passwords Generator and Passwords Saver go hand in hand. Out of the two, the first one is the most functional. There is no special feature available and all the usual options can be used. The application can generate either a single countersign or an entire list (10000 passwords is the furthest I went and the program did not complain). The characters in the countersign can be numbers, lower/upper case letters or special symbols ("!", "@", "#", "$", "%", "^", "&", "*").
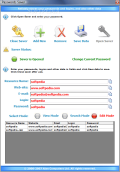
The Passwords Saver, on the other hand, is not as stable as the previous instrument. I experienced a couple of crashes and I could not delete from the list the item I wanted. It prompted me with the "No current record" message.
It was normal for such error to appear as I could not select the entry. I tried do solve the problem by moving back and forth between View and Edit mode in order to select the entry and then delete it. Obviously it did not work.
Invisible Notepad tool is just great. It enables you to create notepad documents and make them invisible. I could not find a way to retrieve the documents other than using Gutnov Cyber Arsenal's tool. They simply vanish in the air. The trouble with this is that there is no way to delete them and upon closing the application you will be prompted to save them or not (despite the use of the "Save" function on the same document).
For a clean uninstall of the software on your machine the program provides an uninstaller with various options. It actually launches the uninstaller of the application and completes the process. The choices provided by this section are editing the entries in the installed program's list, learn some additional information on the selected item in the list (however, many of the fields are marked with Unknown).
The last tool available in Gutnav Cyber Arsenal is the System Manager which allows a comprehensive look at all the processes running on your computer. The star utility in this section is definitely the System Information tool. It presents full information about your system, from operating system, processes running, DMA Channel, BIOS and user Accounts to timezone, system devices, services or boot configuration.
The Good
The Cyber Tools (Encryptor, Surf Cleaner, Eraser, Steganograph and Virtual Safe) and the Password Generator seemed to me the most reliable tool.
The Bad
Much of the new stuff in the software is either not done right (firewall, passwords saver, network analyzer, system manager), not working (iNet Manager) or lacks in options.
The interface cannot be resized in any way and sometimes the tools' windows do not appear in the taskbar. The latter issue results in difficult management and when minimized, the window will disappear (but the process is still running).
The Truth
There is a lot of work to be done from now on. The initiative of the developer is laudable and the tools are indeed a necessity for the majority of the users. However, making the application stable (I experienced a number of crashes during the testing) and providing more options to the user (a help file would also be great for beginners) are issues to be addressed.
Here are some snapshots of the application in action:
 14 DAY TRIAL //
14 DAY TRIAL //