With all types of malware growing more rampant on the Internet, the industry of security solutions for the average user has blossomed to levels never seen before.
Alternatives are all over the place and the game has been taken further than before; apart from relying on the classic signatures to detect malware, it includes proactive protection based on behavior analysis in order to detect even the newest threats, which is sometimes combined with sandboxing for running suspicious processes until their threat level is thoroughly assessed.
However, another breed of programs seems to offer users the ultimate protection level for their systems: virtualization software. This sort of application basically ensures that all the changes to the system are not applied directly but stored to a different location on the disk.
The operating system functions normally, but it does it in a virtual mode that offers the possibility to revert to the previous state, without committing the modifications.
Shadow Defender is such a choice that uses lightweight virtualization to capture all the alterations without affecting the real host. Priced at $35 / €26.33, the application can be tested free of charge for a period of 30 days, with all features enabled.
Getting the program on the system requires some user information, such as user name. Restarting the computer at the end of the procedure is required for all the files to take effect.
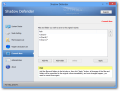
Looks are far from impressive, as the developer chose a simple interface with a clear view of the menus and the options they shelter, and no hidden areas.
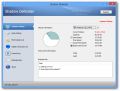
An overview of the system is presented in the main application window, with drive-specific information regarding the current status (shadow mode or not), total storage capacity, amount of used and free space, as well as the portion reserved for storing the changes.
Try&Decide, a light virtualization component in Acronis True Image, offers the possibility to choose any location on the disk for saving the changes made in the virtual mode. In Shadow Defender all alterations are dumped straight on the protected partition.
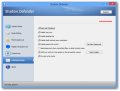
In order to prevent running out of space on a drive, a visual alert is emitted when the value goes under 200MB. This is the default threshold for all volumes, but it is subject to customization according to users’ needs.
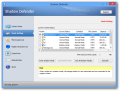
Protecting a partition is just a matter of selecting it and applying the virtualization. The only additional decision to take is whether to maintain virtualization beyond the next reboot (Enter Shadow Mode on Boot) or exiting at the first system shutdown (Exit Shadow Mode on Shutdown). These two actions can also be scheduled.
On the downside, all changes made in the virtual mode are dumped each time Windows shuts down. Keeping a drive’s virtualization past the computer restart will not resume the previous session with all the modifications, but will automatically start a new one from scratch when the operating system loads.
A mark at the top of the desktop makes sure that you don’t forget that shadow mode is currently protecting one or more drives. In some cases, this may hinder user activity, especially when working with applications in full-screen.
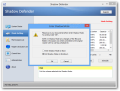
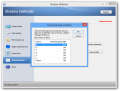
Although extremely simple, Shadow Defender is quite flexible and allows defining specific locations (files, folders, or registry items) to be left outside the protected mode; all the changes in these locations are automatically committed to the original, without any warning.
This list acts as a preset and can be created only with items that are not stored on a currently protected drive. This does not mean, though, that Shadow Defender cannot apply changes on files and folders that are already protected.
It can be done either from the context menu of the item, or by using the Commit Now menu in the main application window.
The operation can take a while in some cases, the factors to be considered for this being the amount of the data to be processed and the available free space. Consequently, it is advisable to commit only small data or to create a proper list of exclusions beforehand. Stopping the program’s protection requires a restart.
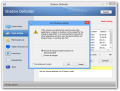
There is little to configure in Shadow Defender. It can be enabled to start with the operating system, as well as to be viewed in system tray for quick access to the interface or to stop all shadow modes.
More important options refer to locking its control under a password and committing changes from the context menu.
Shadow Defender comes in handy not only for keeping malware at a distance but also for testing settings and functions of the operating system or various programs. It also works for those who want to wander in the dark corners of the Internet and remove all traces with a simple computer restart.
The Good
The application is light on system resources and comes with a very mild learning curve. It is easy to use by novices and quite an asset for more experienced users.
The Bad
The application can use RAM as write cache, but I found no way to enable the feature; this may be a limitation of the free trial, but I could not find any details about this.
Update: using RAM as cache can be achieved under Mode Settings, by setting the desired value in the "RAM used as Write Cache" field, before enabling shadow mode for a drive.
The Truth
It works fine and serves right as long as the flaws exposed above are considered.
 14 DAY TRIAL //
14 DAY TRIAL //