Computer networks are all around us nowadays. The connection between computers enables a better communication. The Internet itself is a network, the biggest actually. A network makes file sharing easier and it takes you out of isolation and gives you access to all sorts of information.
But wouldn't it be great if you knew who was connected to your network? I would surely be curious to see the IPs to which I share my files. SoftPerfect Network Scanner is an easy way to satisfy your curiosity.
The software is a SoftPerfect Research product and the version is freeware. The file is only 600KB large and the software does not need to be installed. Just click the executable file and the application will open.
The interface is as simple as can be. With a few mouse-clicks here and there, you can find out who is connected to the network. If those connected have shared files you can access them too and copy them into your computer.
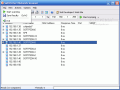
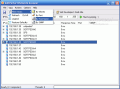
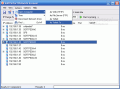
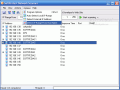
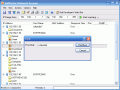
In the upper part of the application window there are the menu bar and the toolbar from which you can access options like scanning the network for connected IPs, filtering the hosts, software's options, etc.; tight below the menu bar and the toolbar there is the IP bar that allows the user to select the IP range of the scanning (type the first and last IP to define the scanning interval).
The largest part of the application window is taken by the result of the scanning. Here the user can see the IP, the host name, MAC Address, response time, port and SNMP (Simple Network Management Protocol).
You can save the list of the IPs as a .txt file. It will contain everything that you can see in the IP scan window plus the names of the shared folders.
Let's scan some of the features the software is endowed with. Besides saving the scanned results as .txt file, the user can also enable applying the shares filter but only the computers with available shared folders will be shown. The same happens if you choose the ports, host name or SNMP filter.
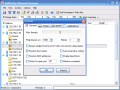
Pressing Ctrl+O will open the Options dialog. In the General tab you can set the maximum number of scanning threads, the ping timeout (time for waiting a reply from a remote computer). By checking the Always analyze host you will force the software to analyze a non-responding host.
In order to see the MAC addresses, you have to check the Resolve MAC Addresses box. The user can specify in here an open port to be checked by the software. If you want the application to display all the hosts in the network (including the dead ones), than you'd better check the Display dead hosts box.
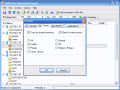
In the Shares tab of the Options menu the user can specify the type of shared resources to be scanned (folders, printers, comm devices, special -reserved for interprocess communication or remote administration of the server, Inter-Process Communication ? IPC or folders and printers).
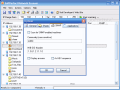
The SNMP tab is for scanning the machines that have a SNMP service running and you can specify a public or private community and a MIB OID number (Management Information Base Object Identifier). In order to see replies from SNMP enabled machines check the display answers box.
In Applications, you can extend the support for third party applications (remote administration or specific client software).
There is no problem if you do not know the local IP range of your network because the software can automatically detect it. The Detect External IP Address can be used if you want to determine your external IP address (if you are behind a router or proxy server).
The Good
The software is very easy to use and does an excellent job in detecting the IPs in your network. The scanning does not take a lot of time.
The Bad
I found an option that is no longer used: connecting to a computer as TelNet. This network protocol was dismissed some time ago in the modern systems because of its vulnerabilities, one of them being not encrypting data sent over the connection.
The Truth
The software does a pretty good job. Do not expect to hack into other network computers as the software stands for another legal way to intermediate the connection between the connected machines. But for some of us, pinging computers and scanning for listening TCP ports is enough.
Here are some snapshots of the application in action:
 14 DAY TRIAL //
14 DAY TRIAL //