Computer security has become an issue ever since computers began to spread to businesses and homes. Every computer user wants to protect his/her machine against all potential threats. The first computer virus is supposed to be a program called "Elk Cloner", written by Rich Skrenta in 1982 and spread by floppy disk. It attached itself to the Apple DOS 3.3 operating system.
The first PC virus was created in 1986 by the Basit and Amjad Farooq Alvi brothers, and was a boot sector virus called Brain. All the virus did was slow down the floppy disk drive and make seven kilobytes of memory unavailable to DOS. But that was only the beginning.
The computer technology has evolved and many people are nowadays confused by the massive infusion of computer terms. Not all of us know the difference between spyware, adware, viruses and worms.
A computer virus is a self-replicating computer program that spreads by inserting copies of itself into executable code or documents. Some viruses do a lot of damage (deleting all the .exe files on your computer, rebooting it every 2 minutes, etc.). The term "virus" is often used to describe all kinds of malware (malicious software), including those classified as worms or trojans.
The difference between viruses and worms is that viruses attach themselves to an executable file on the computer, while worms are self contained and do not need to be part of a program in order to spread.
Spyware refers to a very large category of malicious software designed to intercept or take partial control of a computer's operation without the consent of the computer owner or legitimate user.
Adware (advertising-supported software) is any software kit automatically playing, displaying, or downloading advertising material after the software is installed on the computer or while the application is running.
Spyware Terminator is a computer protecting software from Crawler LLC. It is freeware so you can enjoy it without any restriction. The installation file takes 2.23 MB of your disk space. The interface allows the user to work with the software very easy and it does not have a complicated settings menu.
The language of the interface permits even the least experienced users the maneuvering of the application. The difficult part comes though when you have to remove the objects detected as malicious to your computer.
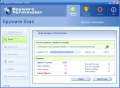
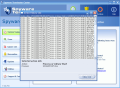
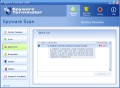
The software scans, cleans and protects your computer against malware. The scanning menu has five options to choose from. The user can do a Fast Scan and the software will check only the important parts of the system; Full Scan performs checks on memory, registry, drives and NTFS ADS. I must warn you that this type of scanning takes a lot of time, computer memory and CPU - in my case it took about 90 minutes to scan almost 50 000 objects.
The user can do a customized scan and choose exactly what the software should check. The options here are virus scan, system, registry and files scan. You can also choose to do a deep files scan and test only infectible files (.exe, .com, .dll) on your drives. The option of scanning only some folders is also available.
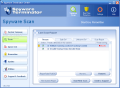
The threats found on your computer can be moved to quarantine or to the ignore list.
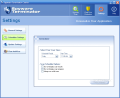
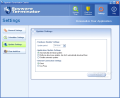
A useful feature of the software is the "system restoration" one. You can find it under Spyware Scan>Utilities. This option is to be used in case of installing or uninstalling programs by mistake. Spyware Terminator creates a system checkpoint before any removal of an application. This way you can restore your system to a previous checkpoint.
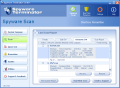
The program provides the user with scheduling the scan task. Simply go into Settings>Scheduler Settings and set a day of the week and a time for the application to perform the scanning of your computer. You can enable/disable displaying the results or running a full system scan. This way your computer will be scanned for malware even if you are not there.
For the software to be up to date with the spyware database the user can set an update period (from one hour to 24). Of course, if you do not want an update you can disable the option.
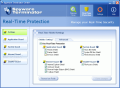
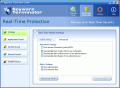
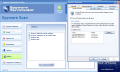
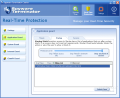
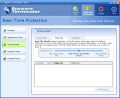
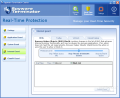
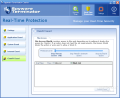
In the Real-Time Protection menu one can set the permission levels for the system, Internet and Clam AntiVirus. Application Guard monitors several important checkpoints and checks for attempts to add or modify your installed applications. It includes startup registry, services and threats.
The System Guard checks for hazardous changes in your computer (security permission changes). It includes system .ini files, hosts file and file extensions.
Internet Guard checks for applications that make unauthorized connections to the Internet or modify Internet connection settings. The options here are BHO (Browser Helper Objects), toolbar, WinSock and IE URL.
The Good
The software is freeware so you don't have to worry about limited features or expiry period. Besides the spyware protection, the program also offers system restoration options. The Real-Time Protection feature is great as it gives you the option of better protecting your machine.
The Bad
I think the full scanning takes too long for an anti-spyware software (~ 90 minutes for 50 000 objects). In full scan the computer is greatly slowed down as the CPU usage is highly intensified.
I encountered a problem when attempting to open a .bmp file in Image Optimizer. The Real-Time Protection feature did not allow me to open that picture. As soon as I deactivated the software I could complete my work (tested four times and the effects were the same).
The Truth
Be careful with the Unknown Software list because it may contain programs that are harmless for your computer. I found my anti virus program in there. Checking the box in the right of the software activates the move to and remove buttons in the lower part of the window.
The software is a good alternative to other programs on the market that do not have so many options and features. I did a full system scan with my anti virus and then with Spyware Terminator and the results were the same (except for the Unknown SW list in Spyware.)
I recommend using it for a couple of days before uninstalling it. You might have a pleasant surprise.
Here are some snapshots of the application in action:
 14 DAY TRIAL //
14 DAY TRIAL //