An advanced memory forensics framework #Memory forensics framework #Digital artifact extraction #Volatile memory extraction #Framework #Memory #RAM
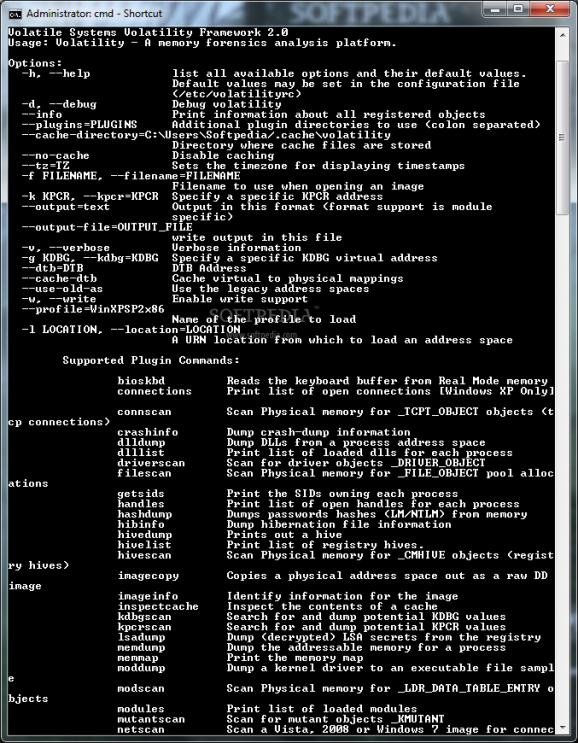
Volatility is a completely open collection of tools, implemented in Python for the extraction of digital artifacts from volatile memory (RAM) samples.
The extraction techniques are performed completely independent of the system being investigated but offer unprecedented visibilty into the runtime state of the system.
The framework is intended to introduce people to the techniques and complexities associated with extracting digital artifacts from volatile memory samples and provide a platform for further work into this exciting area of research.
Volatility 2.3.1
add to watchlist add to download basket send us an update REPORT- runs on:
-
Windows 2008
Windows 2003
Windows 7 32/64 bit
Windows Vista 32/64 bit
Windows XP 32/64 bit - file size:
- 2 MB
- filename:
- volatility-2.3.1.win32.exe
1 screenshot:
- main category:
- Programming
- developer:
- visit homepage
IrfanView
With support for a long list of plugins, this minimalistic utility helps you view images, as well as edit and convert them using a built-in batch mode
ShareX
Capture your screen, create GIFs, and record videos through this versatile solution that includes various other amenities: an OCR scanner, image uploader, URL shortener, and much more
4k Video Downloader
Export your favorite YouTube videos and playlists with this intuitive, lightweight program, built to facilitate downloading clips from the popular website
Zoom Client
The official desktop client for Zoom, the popular video conferencing and collaboration tool used by millions of people worldwide
Bitdefender Antivirus Free
Feather-light and free antivirus solution from renowned developer that keeps the PC protected at all times from malware without requiring user configuration
Microsoft Teams
Effortlessly chat, collaborate on projects, and transfer files within a business-like environment by employing this Microsoft-vetted application
Context Menu Manager
Customize Windows’ original right-click context menu using this free, portable and open-source utility meant to enhance your workflow
7-Zip
An intuitive application with a very good compression ratio that can help you not only create and extract archives, but also test them for errors
calibre
Effortlessly keep your e-book library thoroughly organized with the help of the numerous features offered by this efficient and capable manager
Windows Sandbox Launcher
Set up the Windows Sandbox parameters to your specific requirements, with this dedicated launcher that features advanced parametrization
% discount
7-Zip
- 7-Zip
- calibre
- Windows Sandbox Launcher
- IrfanView
- ShareX
- 4k Video Downloader
- Zoom Client
- Bitdefender Antivirus Free
- Microsoft Teams
- Context Menu Manager
essentials
Click to load comments
This enables Disqus, Inc. to process some of your data. Disqus privacy policy