When it comes to your computer security, it must be tight. I do not know how you feel about this subject, but I would like to know if someone has been meddling with my computer. This is why I decided to look for a software that will protect my computer from intrusive characters, without creating an account and applying a password. I wanted to protect my screen with a single push of a button and go places.
After a lot of hard work documenting on the Web, I found a software that does exactly just that. It protects my screen and restricts the activity on my computer. I did not want to do that, but I have a couple of colleagues that used to have fun on my account by messing with my computer. I guess now I can return the favor.
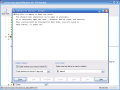
The name of the software is 1st Screen Lock and its purpose (as you probably guessed from the name) is to apply a password to your screen so that nobody can use your computer unless the countersign is entered.
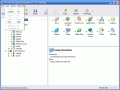
After installing the software, I saw that on my desktop appeared two icons instead of one. The second icon was from 1st Security Agent, a related application that has a lot of uses if you want to block the access to certain features of your Windows OS.
Let's see what it is all about. Installing the software was a piece of cake and I really had no problems with that. The big surprise came when I launched 1st Screen Lock for the first time. All of a sudden, my desktop became black and in the left bottom corner there was a login box that required a password. Luckily I looked in the left upper corner and I received all the details about setting a password for my desktop.
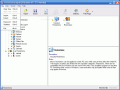
The most important thing is in fact 1st Security agent that contains all the options for restricting the access to certain applications on your computer. This is the place where you need to be in order to apply the desired restrictions.
In the left side of the application window, there is the Restrictions tree that contains Common Restrictions and User Restrictions.
The Common Restrictions shelters options related to Boot, Automatic Logon, Screen Lock, Legal Notice, Network, Explorer, Internet, System, Offline Files, Remote Access, Scripts and Software (Outlook Express, Media Player, Microsoft Office and MSN Messenger options).
Each of these submenus contains a series of options designed to help you restrict the access to lots of Control Panel functions. Security restrictions can be applied universally or to specific users. To give you some examples of what you can restrict, I will tell you that you can use the Always Check Password on Boot under Boot in order to lock the PC by starting Screen Lock on boot of the system.
Another restriction is Disabling the Safe Mode and do not be worried if the system is crashing every time you boot it in Safe Mode while the restriction is applied. The crash is just a consequence of the restriction.
In Network, you can hide user accounts from the logon screen or disable password caching. In a network hidden shares are common. With 1st security Agent, the user can disable automatic hidden shares and even hide share passwords with asterisks.
In Explorer, the user can choose to hide welcome screen or hide Send To from the context menu. And if you really want to put spying persons into trouble, then you can disable the main menu bars and the start button or remove the items from the start button context menu.
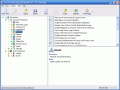
In User Restrictions, things are not as easy as in Common Restrictions as the options are almost twice as many. You can apply restrictions to the Control Panel items like Add or Remove Programs (disable the feature, disable Add Programs, disable Change and Remove Programs, etc.), Display (deny access to the Display Settings, hide Themes Setting Page, etc.), Printers, Internet Options and Applets (the myriad of options in here includes hiding the Internet Options in Control Panel, hiding User Accounts/Add Hardware/Accessibility Options, etc.).
User Restrictions, as the name suggests, includes options that are applied for each user account available on the computer. The options are exactly the same, only they are restricted for each user.
A nice feature of the software is the Statistics one that can store all the actions of a specified user. It is in fact a built-in spy that displays statistics of working of the users. A kind of log file that includes the application that was launched and the time of the launch.
The Good
The software contains lots of useful options that will strengthen the security level on your computer. Almost everything can be restricted with this software. In order to protect all the settings, you can apply a password that will restrict the application's launching by unauthorized users.
The Bad
The welcome screen is pretty negative and the fact that the developer announces me that "We guarantee that most of restrictions will work on your PC as advertised" does not give me too much confidence for using the software.
The Truth
I really liked the software, despite the fact that I do not know the trial period and the price.
Here are some snapshots of the application in action:
 14 DAY TRIAL //
14 DAY TRIAL //