Lavasoft has recently updated its security batch of products to a new version. And this year the company upped the ante including their full antivirus in the free version and creating a full blown protection suite to encompass not only Lavasoft’s best services, but also something on the side. Although there is no longer a Plus version of the application, there are still three editions available.
This year’s Ad-Aware installs are Ad-Aware Free, Ad-Aware Pro, which remains practically the same in terms of design and feaures, and Ad-Aware Total Security. What used to be the best, the Pro edition, is now superseded by a totally redesigned suite, which comprises an entire arsenal of tools designed to help you block malware from infecting your PC and pluck active threats out. Backup and restore functions, web protection, anti-phishing measures, email safety, anti-spam, parental control or system tuning options are all present in the bundle.
As expected, Ad-Aware Total Security, on which we’ll be focusing, has the highest price in the bunch, $49.95 for one year single user subscription. Pro edition is cheaper, at $29.95/year. However, both of them can be taken for a spin for a period of 30 days, with all features working regularly.
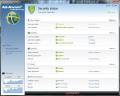
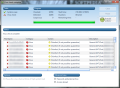
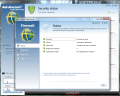
The application is like no Lavasoft product you’ve ever seen: five categories and their sub-menus available straight from the main application window, which is resizable. Even more than this, links to the options for each of the listed menus are also present in this space. On top of all this, the current state of all the engines and protection layers included in the suite is visible from the main screen. Basically all you have to do in order to adjust some settings or view how everything’s running is fire up the main application window.
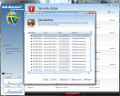
Virus check
The two engines in charge with scanning in Ad-Aware Total Security (yes, dual-engine structure) can be enabled to run simultaneously or only one of them, depending on the detection power you need. They are currently named Engine A and Engine B, but they stand for Lavasoft’s own and licensed G Data engine. Running them in tandem is the default configuration and a very smart choice judging by our testing.
Our malware database of 16704 samples has been scanned completely in 12’24’’. The amount of left over threats reached the number of 499, which translates into an incredible detection accuracy of 97%. Although our samples are not the freshest in the basket, there are some pretty nasty items among them which posed serious trouble to renowned antivirus solutions on the market.
We noticed that CPU usage during the process was pretty high, with an average of 80%. Fortunately, this should be no hindrance for you if you want to work on the computer while Ad-Aware is scanning because the application comes with an option to put virus check on pause when system load is too high.
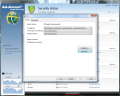
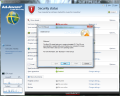
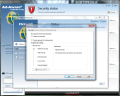
Setting up the actions for this category is no tough job, regardless of your computer skills. Real-time protection and behavior monitoring as well as the priority of the scan engine and file types that should be verified can be configured from the Options window. Moreover, you can impose different actions when encountering a threat: log only, disinfect (if not possible: log only), disinfect (if not possible: quarantine), disinfect (if not possible: delete), move file to quarantine or delete it right away.
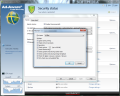
Additional functions available in the category include scheduling of virus signature updates (as fast as one hour apart) and setting up the frequency of automatic system scans. As far as the latter are concerned, they are customizable in terms of targets to analyze (local volumes, memory and startup or specific files and folders), engines used, reaction to threat detection and user account (if network drives available on the PC also need to be checked and require authorization).
Access to Quaratine is also part of this category’s extended set of functions. Regular options are available, such as submitting items to Lavasoft laboratories for a more detailed analysis, purging the quarantine of all detected elements or their restoration to the original location.
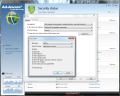
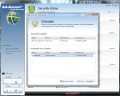
A premiere in Ad-Aware products is the possibility to create a bootable CD (the option is not included by default during the application’s installation process). The benefits of this option are obvious if you try to clean a system infected with threats that do not permit the installation of an antivirus solution. The entire procedure is performed with the help of a guiding wizard which also provides advices so that the resulting disc is equipped with the latest signatures available from the developer.
Internet
Getting infecting simply by navigating to the wrong page is not at all uncommon these days, just like it isn’t to receive infected files over your favorite IM program. These two issues are tackled in this category under “Web protection” menu, together with anti-phishing protection and firewall security.
We tried to double-cross Ad-Aware Total Security with a set of carefully selected phishing addresses but it seems like the developers took care of this aspect because we almost failed miserably. Almost is the key word here because we managed to find one example that escaped Total Security’s vigilance and let it load. However, out of the 20 examples we found only 10 were still fresh and very much online because in the case of 9 of them, all registered with the same hosting service, their accounts were suspended. This means that the program succeeded to protect us from 9 out of 10 addresses leading us into a trap.
In the case of the threats coming through the HTTP chute, these were instantly blocked. Given the high detection rate during our on-demand test this result came as no surprise to us. Exceptions can be set if you want to access an address which the app blocks, but if the content you are trying to download is infected, expect interception from the real-time protection engine.
Configuration for these two comprises a simple but important set of options, which allow you to enable or disable processing of Internet and IM content and set the server ports. Additional choices to help you to a compromise between performance and accurate detection allow you to set the download limit of the files or enable transmission of the infected websites to Lavasoft labs.
The firewall included in the suite is also listed under Internet category. As much dreaded as this sort of instrument is by beginner and average users, in the case of Ad-Aware Total Security this tool combines simple configuration through preset protection profiles with custom security so that professionals have a chance to define rules.
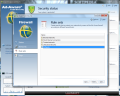
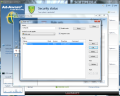
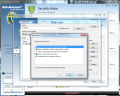
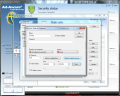
Creating rule sets to protect your network is a simple task even if you are not an experienced user because Ad-Aware Total Security makes available a wizard to guide you through creating the rules. You can choose between allowing and blocking a specific application, open or disable ports, allow/deny file printer sharing, allow/deny domain services or enable Internet connection sharing.
What is interesting when creating an application rule is that besides customizing the connection type (inbound, outbound), access and protocol, the firewall also makes available the possibility to select a time window. This means that you can prevent applications from communicating with remote servers on specific days of the week and between specific time intervals.
We put the firewall to several tests to check it for leaks. Unfortunately it did not pass all the leaks tests, but it proved that it can stand for pretty solid protection. It failed PCFlank’s leak test but it passed the exploits test. Checking typically vulnerable ports the firewall succeeded in stealthing all of them. On the other side, random verification of ports showed in some cases that they were simply closed, not stealthed.
NEXT |
This article is also available in Spanish: Ad-Aware: potente suite de seguridad (I)
Follow me on Twitter @Ionut_Ilascu
 14 DAY TRIAL //
14 DAY TRIAL //