File encrypting is certainly one way to safekeep your data from prying eyes. The process of encryption is not at all complicated if you know where to look for the right software to do it with. The first thing you should look for in such a software - in order to learn how secure the encryption is - is the number of encryption algorithms supported. The larger the variety, the better.
PowerKey is the $24.95 data encryption solution from Elcor Software. The software can be fully tested and all the options explored with no exception, as the 14 days evaluation period is the only restriction applied to the trial version.
Concerning the reliability of the application, there are no problems here as PowerKey provides a suite of eight encryption algorithms to choose from (Blowfish, 3DES, Cast-128, DES, Gost, RC2, Rijndael and Twofish). These algorithms are pretty known and very reliable, especially for home use.
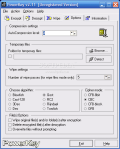
The developer clearly sacrificed the looks of the application in favor of its functionality and efficiency, as the interface is Windows 98 like. The only proof that the program is not that old is the background of the context menu in the menu's options. The tabs displayed in the application window cover every option made available by the application. Besides encrypting the files and folders for restricting the access of unwanted persons, decrypting option is also present.
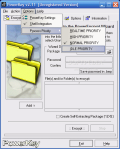
Additionally to these options, PowerKey features a secure wipe option that allows you to overwrite the free space on the volumes installed on the machine to prevent recovery of sensitive data. The option works fine if you want to secure delete files present on your disk. The number of passes can be set in the options menu and go as up as 200 overwrites.
I tested the application using the maximum number of passes on a total of 2MB. I must say that the process did not take as long as I expected (only 49 seconds for both of the files) and worked like a charm. On wiping the free space of a disk, the operation took longer (1'31''), but the result was also a succes.
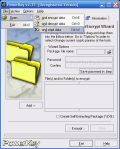
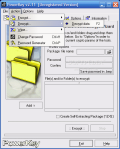
Encrypting your data is also done speedily and the operation requires providing a password and setting an encryption algorithm in the Options menu. One new element you will not find very often in similar softwares is saving your password in a BMP file. This way, your decryption should be made even if you lose the password. I stress "should", because during my tests, this feature did not work and although I loaded the right picture I was still asked for a password.
Down the window there is a little box that reads "Create Self-Extracting Package". Checking it results in creating an EXE file that once executed will prompt you with the password for extracting the secured file. The encryption process is also useful when you want to save some space on your computer because the encrypted files will be heavily compressed. Regarding the password, you will have to enter it twice. Advanced computer users and even average ones will try to get to the second field by using the TAB key. Unfortunately, the effect will not be the expected one, as TAB key will be treated as a character of the password.
Going to Options menu, the user gets the chance to configure the software. The auto-compression level can be adjusted from the default level of 4 to 9. The temporary files the software has to make are located in the Local Settings folder, but the user can change it to a more convenient location. Wipe settings comprise only the number of passes for the overwrite operation.
Algorithm choosing is a serious job and the developer provides additional information on each encryption method. This way you can choose the one you think offers the best data protection. Cipher mode (CFB-8bit, CBC, CFB-block and OFB) on the other hand does not measure up the encryption algorithms as they are not ensuring message integrity and only confidentiality is secured. Some more up to date solutions would be CCM, EAX and OCB. Despite this little mischief, your data is as safe as it could be because a hacker will spend a he(a)ck of a long time striving with the brute force method and eventually will give up.
The flexibility of the application allows enabling deleting the original files and folders after the encryption is complete. The same option is available for encrypted files after the decryption is finished.
The Good
Very nice application if you put aside the looks and the price. There are eight encryption algorithms that make a good compromise in what concerns speed and security.
Auto-compression level can be set as high as nine.
The Bad
It's a pity that hiding the keys in BMP files does not work properly. However, you always have the password option to use. The price is pretty high considering the looks and the little drawbacks.
I am still longing for an option that prevents deleting the encrypted files from your computer. Setting a password for launching the application would make the user feel a bit more secure about the protection of the files.
Adding a "Rename before overwrite" option would greatly increase the value of Wipe function in the software.
The Truth
Nice and easy to use application. The trial period is 14 days long and there are no other limitations applied.
Here are some snapshots of the application in action:
 14 DAY TRIAL //
14 DAY TRIAL //