Keyloggers are nasty little cyber-critters. Although they themselves do not cause any harm to your computer, they put all your privacy in the hands of a third party that remotely controls them. The sole purpose of a keylogger is to record all keystrokes on a computer and transmit this information to a remote location; and that's how all your private conversations or documents are disclosed without your knowledge.
However, installing one keylogger yourself can prove to be a good way to protect your computer, detecting breaches and laying up a counter-attack plan. Such a critter can turn into a utility tool if you want to monitor the activity on your computer in your absence. The "assailants" may even leave behind information that could backfire against them, like conversations or a password. In any case, you will know what happened while you were gone and the measures to be taken are entirely up to you.
AllSpyMonitor can become an important ally if used wisely and properly. Its purpose is to record all keystrokes and take a picture of the desktop every once in a while (actually, the user gets to set the frequency of taking snapshots of the desktop). Although there is similar software that is freeware, AllSpyMonitor comes at a $24.99 price and with quite a set of limitations.
The application does not feature complicated options and it can run surreptitiously on the system, tricking even a skilled user. AllSpyMonitor installs easily and effortlessly, leaving no icon on the desktop, thus making itself almost invisible. The only trace is a folder named "allsm" in Program Files, which contains all of the software's installation files.
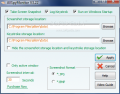
Making the necessary configuration settings should not take too long as there is little to set up and the defaults work great. AllSpyMonitor provides two different monitoring options, taking timed screenshots and keystrokes recording which, combined, can give you a strong hint on the activities your computer was used for. You get to define the locations for storing this data and you can even choose to hide the location. By doing this, there are little chances for someone to find the location and delete the recordings, as it stays hidden even in Windows Explorer, and changing the default location will definitely keep the files protected (in addition, the intruder would have to know what program you are using).
Once AllSpyMonitor is started, there is only one trace that could give it away to a more experienced user, and that is its process. It does look suspicious and it made me dig deeper into the matter the moment I saw it in the Task Manager, but the fact that I knew I was looking for something suspicious in a very familiar environment hugely contributed.
The name of the process is "nvsvc16" and, in Vista, it will be shown as belonging to an application with the same name. You need this information in order to stop the monitoring activity, and terminating the process is the only way to do it.
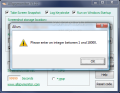
All the image logs of the computer activity are stored under JPG or BMP format. In fact, they are all taken as BMP and then converted to JPG to save some disk space. The user gets to set the frequency of taking the snapshots, which is defined in seconds with a value between 1 and 18000. Running the program at Windows startup is checked by default and leaving the option enabled would ensure that AllSpyMonitor records all the computer activity in your absence.
As installation folder is not protected in any way, the access to application's settings is password protected, so that unauthorized persons are not allowed to make any change. The downside is that a countersign of exactly six characters is mandatory as the program does not accept passwords longer or shorter than this.
Reading the recording of keystrokes may be a bit of a challenge at the beginning, especially if the original writing is filled with backspaces as the "transcript" will contain additional characters marking all the keys. The report is saved in TXT format so you can open it on any computer with absolutely no difficulty. The downside is that the log does not mention closing applications, only which one is opened; the recording of copy/paste operations is marked only by blank space as the writing is not captured (that's why combining the two methods have better results).
The limitations of the trial version of the software do not allow hiding the screenshot and keystroke storage location and you cannot set the program to capture only the active window. Also, protecting the access to the settings with a password is not allowed and the number of snapshots is restricted to three (anything beyond this will be partial) while the file for keystrokes stops at 500KB. But unlocking the full version all these restrictions are eliminated and the app does what it has been designed to do.
The Good
AllSpyMonitor does a great job with spying the computer's desktop and keyboard, providing easiness of use in configuring it and pretty good invisibility.
It can hide the storing location so that no one but you knows where it saves all recordings. The settings window is password protected for enhanced security.
Desktop recording interval can be set by the user anywhere between one second and 300 minutes.
The Bad
Considering all the options available, I was expecting a lower price or at least an option for sending the reports/logs to an email box to be included. This way you would be given the opportunity to monitor the use of your computer while at work or away from it.
The process can be identified by a more experienced user looking in Task Manager.
The Truth
AllSpyMonitor will do its job and keep its activity as stealthy as possible. It records keystrokes and takes desktop screenshots in order to provide the most accurate log of computer activity. When opening new apps, it will mark them with their name as well as time of the day.
However, it would be nice to have an option that automatically sends the reports to an inbox if the user desires. This way you can learn if your computer is used and how it is used, while you are at work.
Here are some snapshots of the application in action:
 14 DAY TRIAL //
14 DAY TRIAL //