Expert Mode
Novice and Intermediate interfaces are anything but suitable for an experienced user that wouldn’t feel content unless they manage each aspect of the suite. Computer experts have their way in BitDefender’s Total Security through Expert Mode, the GUI that reveals all the features of the bundle and offers the possibility to customize each of them.
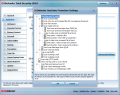
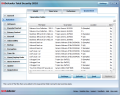
The modules stacked in the left hand part provide all elements a user would expect from a complete security: antivirus, antispam, parental control, privacy control, firewall, check for outdated software and vulnerabilities, data backup, file encryption or PC maintenance. Additionally, there is the possibility to customize the behavior of the suite the moment you launch a game or your laptop is running on battery.
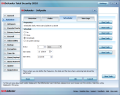
You’re going to witness the full flexibility of this interface right from the first menu, which covers general settings. The dashboard information is richer and includes the amount of files scanned, number of infected files, as well as time of the last scan and update. An important option is password protecting BitDefender’s settings area in order to restrict access.
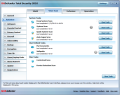
Precious information about the operating system, current registry settings and installed programs can be obtained under System Info panel. You’ll be presented details on startup items, file associations, services, components under Windows Explorer, as well as under Internet Explorer, or the full list of currently running processes.
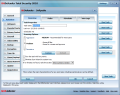
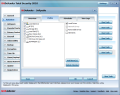
The antivirus section is fully configurable in what concerns aggressiveness of the engine, which controls the detection rate, scan types and their schedule and locations that should be excluded in the process. Access to all quarantined items and making the arrangements for their automatic deletion is available under the Antivirus menu.
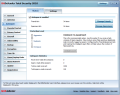
One important aspect is the configurability of real-time protection provided by BitDefender. An experienced user will appreciate the flexibility of setting this up as practically every aspect can be controlled, thus creating your own level of scanning that includes the type of files and apps that should be checked, malware to be scanned for and actions to be taken against a detected threat. The scan engine can run tight security and have a look even at incoming/outgoing emails, or check web traffic or data sent over IM (Yahoo! or Live Messenger).
Putting to the test BitDefender’s capacity of detecting and eliminating malware on an infected machine showed great results, although not the best. Out of the set of hand-picked malware (spyware, Trojans, viruses, backdoors and rootkits) and some files that are generally wrongfully picked up by security solutions as threats, BitDefender managed to detect and quarantine 72.5 % of the threats, leaving the good files alone. The number may seem low, but compared to other antivirus products, this score is actually among the highest we have recorded.
Antivirus in BitDefender security software is generically used to define all sorts of malware, and is also the place from where you can enable anti-phishing protection. It works great under Internet Explorer and Mozilla Firefox, as well as Yahoo! and Windows Live Messenger. The only form of management for this is creating a whitelist in case of false positives. However, in our case, out of the 21 phishing websites we faced BitDefender’s anti-phishing capabilities against, all pages that opened were recognized as scam attempts as soon as they finished loading.
On the downside, you will benefit from this sort of protection only under Internet Explorer and Mozilla Firefox, if you have either of them on the system when Total Security 2010 is installed. If you install Firefox after BitDefender’s security software, in order to benefit from anti-phishing toolbar, you’ll have to restart your computer. At the time of writing this review, AntiPhishing toolbar from BitDefender is not compatible with Firefox 3.6. I’m sure the problem will be solved, but it’s been more than ten days since Firefox 3.6 was released and no fix from BitDefender.
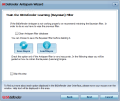
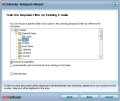
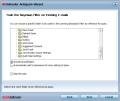
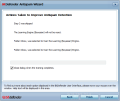
Anti-Spam module has plenty of tweaking a power user can toy around with yet it is extremely easy to set up. Its efficiency has been noted since the review of the beta release of the product. At the first run of the engine, the application will run an optimization wizard to guide you through the process of training the learning filter (if your email client of choice is Microsoft Outlook, Outlook Express, Windows Mail or Thunderbird 2.0.0.17).
With spamming and email scams evolving at amazing rates, segregating these from legitimate messages becomes a pretty difficult job. BitDefender’s antispam component relies on Bayesian learning and blacklisting/whitelisting email addresses. Doing some testing on a legitimate message database, the component proved that it leaves little room for false positives as detection was of four messages out of the total of 671, which translates into 0.6% inaccuracy in the case of legitimate emails.
However, when faced with an inbox containing a total of 61 emails, both spam and valid messages, BitDefender’s accuracy decreased, letting 14 villainous messages through and accurately marking 16 of them as spam and sending them to the appropriate folder (Junk or Spam). Notable in this case is the fact that none of the valid emails was wrongfully labeled.
One problem that may seem difficult to tackle is represented by spoofed email addresses. Yet training the Bayesian filter to discern between spam and valid emails (during the training session, you will be asked to point a location with spam messages and one with valid ones) will do the job.
The module integrates perfectly in the supported software as an add-on, giving you access to the settings list. Configuring the component to work the way you want it is just a matter of enabling or disabling the desired functions. Sure, you will have to check among the spams from time to time, but there are little chances to find a valid message in there.
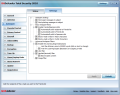
Privacy has never been more under attack than these days. It seems like everybody with a computer is bent on snooping on your browsing habits or out to get hold of sensitive data such as passwords, SSNs, PINs and the like. Privacy Control under Total Security is designed to prevent such information from being disseminated without your agreement. The four sub-modules available offer protection for personal information, against registry intrusions, cookies and script control.
To put it shortly, identity data (email, addresses, passwords, credit card and bank account numbers, names, PINs, SSNs or telephone numbers) will not leave your computer through HTTP, SMTP (email) or IM (Yahoo or MSN) traffic. Emails containing sensitive info will not be sent, just like websites and IM messages won’t be allowed.
Registry Control monitors Windows Registry and alerts you at any modification attempt. If you do not recognize the program trying to change the registry, BitDefender will pop an alert and you can simply block the action. The same principle is applied in the case of cookies and scripts. However, as plenty of websites send them to users, creating rules is the only way out, although still pretty nagging at the beginning.
The firewall is a strong component in any security suite, and BitDefender’s protection against inbound and outbound unauthorized connection attempts works like a charm. Long gone are the days when you had to interrupt your work every five seconds just to deal with another popup. Not the case with BitDefender’s firewall, which is governed by a comprehensive list of safe applications. Programs not on the list will trigger a permission dialog.
Rules are created automatically so you won’t have too much to configure, unless you need special ruling. Extreme granular control is offered for the matter, to the point of defining the adapters an application is allowed to run on, local and remote addresses, ports and protocols. But this is the advanced part. By default, you won’t have any trouble with the firewall save from creating new rules for the programs outside its whitelist.
As for cloak-and-dagger activities, these are doomed. Ports are properly concealed and information leakage was unsuccessful during our testing. Each time a test program tried to send information, we were alerted and asked for permission.
 14 DAY TRIAL //
14 DAY TRIAL //