The Internet is filled with software making promises to better protect your privacy, erase your web-browsing traces and keep all personal data away and safe from prying eyes. Unfortunately, very few of them rise up to the ease-of-use standard you are comfortable with.
All your data, once deleted from the disk, is actually still accessible either through methods involving specialized software or by using hardware methods. That happens because the actual information is not at all eliminated from the hard disk, but tagged by the system as free space, as only its name is being erased. Thus, when new files are added, the system will provide the “free space” and the old data gets overwritten, hence harder to be recovered.
If you're looking for ways to make your information completely irrecoverable, regardless of the method used to get it back, then give East-Tec Eraser 2009 a try. It comes with a 15-day trial period with full functionality of the application and its aim is to securely erase all deleted data on your system. The type of information it affects includes anything from files and folders to email messages of some of the most used clients, web browsers or data left behind by various apps. Despite all its data-erasing capabilities, the price on its tag will remain $49.95.
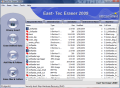
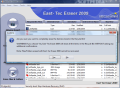
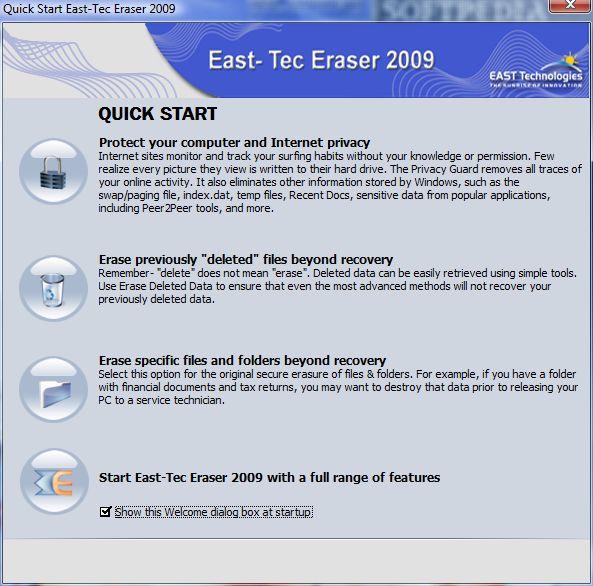
When launching the application for the first time, you will be welcomed by the Quick Start panel, which is an easy way to put the software to work its magic on the system. It provides a set of three options for accessing the Privacy Guard module (removes all traces of your online activity, info stored by Windows and sensitive data from popular applications), to erase previously deleted data (wipe free space) and user-defined files and folders beyond recovery. Closing this dialog box lets you access East-Tec Eraser 2009 itself, which provides a tad more.
The interface is simple and comfortable to work with, not at all crowded with options and menus. You will notice a blank window flanked by a set of menus arranged both vertically and horizontally. It looks pretty odd, but there is no disfunctionality. This is where you get to add files and folders to erase beyond recovery. A simple drag and drop of the desired items will ready them for the process in no time.
Process Guard
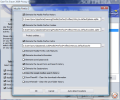
East-Tec Eraser 2009's Privacy Guard is one of the core components of the application, as it features no less than five sensitive areas it can deal with, plus a user-customized component that basically lets you create your own area targeting specific locations and data. The module comes in two flavors, a basic one that automatically runs all the defaults and an advanced one that allows user input for the settings and options.
Going “advanced” with the module will put you in front of six tabs (Windows, Browsers, Applications, Peer2Peer, News and Email Reader and Custom), which you can configure your own way. In Windows, the software provides a plethora of options for you to tick in order to sentence all the data they hold to oblivion. All the data included here is sensitive information Windows holds on the system without your knowledge or permission.
Listed under this tab are choices like cached fonts, memory dumps, recently used documents, stored application descriptions, temporary files, the Run menu list, the Windows clipboard, the swap file, scandisk file fragments, etc. Once started the deletion process, depending on the wipe algorithm used, none of the data can be recovered.
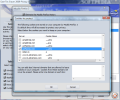
Under the Browser tab, the program displays the browsers you have installed on the system and lets you select the ones in which it should delete the traces of Internet activity: history, cookies, cache data, temporary files. From what we've seen, it supports all popular web browsers on the market and, in our case, it successfully detected the installation of Google Chrome, Internet Explorer, Mozilla Firefox and Opera.
In fact, it will show in the list only the newest version of the browsers it detects on the system, nothing more, nothing less. If you're a fan of an older edition, there is the possibility to select your choice from an old version list, which includes AOL, Netscape, and former editions of Opera. For each of the selected browsers, you get to tick the data you want to be securely eliminated, as well as define the paths for history, cookies and cache folders.
In the case of Internet Explorer, Google Chrome and Mozilla Firefox, the granular control goes as deep as selecting the cookies to be protected and kept during the deletion process. Even more, the application lets you define the domains that are allowed to leave cookies on your computer. This way, the cookies from the defined domains will never be erased.
The list of applications included in East-Tec Eraser 2009 is pretty huge and comprises the most varied palette of software, from antivirus software, video players, office suites, or file managers to instant messengers, audio players, file-archiving software, FTP clients, image editors and download managers. As in the case of web browsers and Windows data, the moment you tick a checkbox, a new menu will pop up, providing the elements that will be dealt with.
Exactly the same approach is maintained for Peer2Peer programs, which gather a suite of 19 such applications among which we count uTorrent, BitComet, old Emule, Limewire, Kazaa, MP3 Rocket, and many more.
Under the “News and Email Readers” tab, there are also some of the most popular email clients and RSS readers (Windows Mail, Agent Newsreader, EarthLink, Eudora, Mozilla Thunderbird, News Rover and Outlook Express 6). This list, however, should have been more comprehensive, considering that there is plenty more to be added. Again, selecting the data that will be deleted is left for you to choose.
If some applications or Windows locations are not listed in any of the aforementioned five menus, the Custom tab will fill in great. This is the area where you have total liberty in adding new areas to be wiped clean. It supports adding single files, a bunch of files in a folder, entire directories and even registry entries.
Having selected all the data to be safely and securely eliminated, you can proceed to the step precursor to the actual deletion, where more options await. Two, to be more exact, and they consist of automatically restarting the computer in order to finish the process and enabling the scrambling of file and folder properties. I suggest keeping the latter ticked, as it will create a mumbo-jumbo out of file names, creation date, size, and all. You may get the “low disk space” warning when this option is enabled, but it can be safely ignored as it pops up because, in East-Tec Eraser 2009, everything is overwritten and all space will become available after the operation ends.
Erase Deleted Data
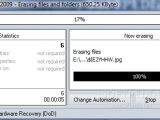
Wiping the free space is another component in East-Tec Eraser 2009's arsenal of features. The module is designed to help you destroy all files that have already been deleted, and, during the task's run, no live information will be affected in any way.
The module's menu shows all drives present on the system, regardless of whether they are removable or fixed. It even shows virtual folders. With a single click of a button, you can check all local drives or all the entries available. Lower in the panel are the wipe settings that let you enable wiping either the free space, or the slack of existing files, as well as scramble the properties of deleted data and system transactions log (on NTFS drives).
But the big league options are available under “Erasure Settings.” Here's where East-Tec Eraser 2009 excels and raises above other data-erasing software on the market. The wipe options armory contains, besides the standard wipe algorithms encountered in so many secure deletion software, some of the most powerful sanitizing methods available.
From the single pass ones that finish fast and offer a low security level as they only prevent software from recovering software, to the hard core ones such as Gutmann's 35 pass method, the application has them all, and then some. Just to enumerate several of them, East-Tec Eraser 2009 provides the AFSSI-5020 (USAF Cryptologic Support Center) algorithm derived from DoD 5220-22-M (US Department of Defense standard), US Navy's standard (NAVSO P-5239-26 with 3 passes), Russian GOST, German VSITR, Bruce Schneier's 7 pass algorithm or the 3+7+3 Beyond DoD Standards.
Some of them do not put up with data recovery via hardware tools, but all of them can successfully protect you against data-recovery software. As you scroll down the list of algorithms, the security level and the duration of the process completion drastically increase. Also, all algorithms are briefly presented, but concise, regarding their actions as soon as you select them.
The surprise in East-Tec Eraser 2009 is the possibility to create your own data-erase algorithm with as many passes as you want and define each one your own way. The options in this sense include picking the byte/text pattern, defining a list of random bytes or characters. If there are more than two passes, you can shuffle them for a better overwrting. Also, each pass can be checked for correct completion. Thus, you are given the opportunity to create your own data-erasure method and add a name to it, as well as a description.
| Next
 14 DAY TRIAL //
14 DAY TRIAL //