Back in the old days, trust wasn?t a virtue, like it is in the present, and in order to keep a moral stand one didn?t have to do much. But now you can?t trust anyone until proven innocent beyond any doubts.
There are many spineless inconsequentials that don?t care too much about these ethical issues, and would lie, trick and deceit people continuously, showing no penitence whatsoever.
An old proverb says ?if you can?t fight them, join them.? A program that will help you either be one of these trivial individuals, or catch them red handed, is SC-KeyLog PRO. The main purpose of this program is logging all the activity on your computer, including passwords, clipboard activity, websites visited and so on.
Your secret's safe with me... Is it?
This is the perfect program for you if you?re an employer and see an efficiency dwindling in your employees (which may be dwelling in Internet surfing and not working most of the time), if you suspect that your partner is involved in extra conjugal activities, or just want to find out more about your room mate?s personal life.
The program?s interface doesn?t excel in design and creativity, but it?s friendly enough so that you will get the hang of the program?s functions and options from the first time you use it.
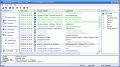
You basically do all the work from the SC-KeyLog Control panel, which is divided into three sections: Tasks, Status, and Operations.
The tasks section allows you to change the program?s master password (which will be asked whenever you enter the program).
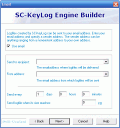
The program doesn?t actually do the logging work, but it creates logging engines that do this. For this, you have a wizard that will assist you set up the engine better. What?s useful about this program is the fact that it?s able to log the activity of a remote computer, and not only the one that?s installed on.
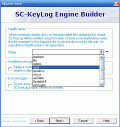
The engine is an executable process that is easily detected by the user in the Task manager, or any other similar application. But the SC-KeyLog allows you to select a stealthier engine name (and provides a few samples: iexplorer, iftp, mdmm, spoolsvc, up2date and some others), thus it lets you ?hide? the program (it?s not actually hidden, but its name tricks you into believing it?s a clean one).
Also, you can edit the default icon to a more ?innocent? one, so that no clue about the program?s profile is given away.
You can have the logs sent to your e-mail account directly by the engine. You will have to configure a SMTP account, so that you can receive your e-mails promptly.
The program allows you to select the time intervals when you should receive the logs, and as an extra filter you can have the log file sent to you once it reaches a certain size (some e-mail accounts reject e-mails larger than x Mb, so this option is welcome).
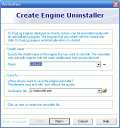
Just as easy as creating keylog engine, you can create an uninstaller that will help you remove all engines from your computer.
The status section provides information about the KeyLog engine: whether it has been created or not, and whether it is running or not.
Then, moving on to the Operations part of the window, you can notice four actions that you can perform: view the current logfile, clear current file, Start/Stop engine and Remove engine.
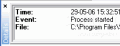
When viewing the logfile, you are presented with a list containing detailed information about every single move that?s been made on the target computer. The information that?s shown is categorized by Date/Time, Window title/Info and, the most important one, Logged data.
The logged information is shown as a string of characters, combined with the actions that you?ve performed. The program logs all passwords too, but you won?t know what information goes in what field (it records only the keyboard strokes, and clipboard activity).
There?s not much to say about the clear current log, Stop engine and Remove engine actions, because their result is exactly their name.
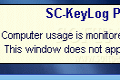
A plus to the program is the fact that once you?ve minimized it, you won?t be able to switch back to the window (the Alt+Tab key combination doesn?t track it, and there?s no icon in the system tray) until you run it again.
In this demo version, whenever the engine is recording the activity, there?s an information clip in the bottom right portion of the screen that?s shown in front of all applications, and warns you that the computer is being logged. This means that if you want to really spy on someone, you must buy the full license, which costs $49.50.
The Good
The program is fun to work with, and the fact that you can create key logging engines that are customizable (and small in size, taking up only 102KB) makes the program both undetectable and easy to install. Also, the remote logging feature allows you to easily monitor the activity on a distant computer, without having to install the whole program on the target machine.
The Bad
The demo version continuously displays an information clip that warns the ?victim? about the privacy hazard. Also, the format in which the logs is presented makes it a little bit hard when you need to interpret the data into comprehensive information.
The Truth
It?s easy to configure the application, and anyone can do it in a matter of seconds. Even though the interface isn?t a beauty contest winner, it gives you good command of the program?s features. The demo version is merely for testing purposes, but if you get your hands on the full version, there?s no secret that can resist you.
Check out the screenshots below to get a glance at the program in action:
 14 DAY TRIAL //
14 DAY TRIAL //