Steghide UI is an interface created for steghide command-line tool which is designed to hide various data in image and audio files. As command line is generally avoided by regular users, Steghide UI comes to correct the problem by offering a clean interface any user can handle with ease.
Encrypting data so that only the intended recipient can read it is a pretty common practice these days. But if you want to send them in a stealthy manner so that possible interceptors don’t even realize what is going on right under their noses, steganography is one easy way to achieve this.
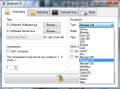
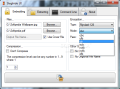
The elegant interface provided by Steghide UI permits any sort of user easy access to steghide’s options, which are simple, but powerful. This interface gathers all the features of the original program two tabs from where you can initiate the process of disguising your files and extracting them.
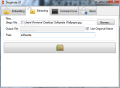
You have to know from the start that the file formats you can rely on to embed the secret data are BMP, JPG, WAV and AU, which are called cover files. You won’t be able to disguise your data as any other formats. Our tests included both image formats and WAV audio file.
As far as the embedded files go, these can be anything you want, but keep in mind that they will modify the size of the container, and in most cases this can represent a good reason for further investigation of the file. However, the information that can be obtained is that there is a hidden file contained, because the encryption algorithms are some of the best standards currently on the market.
Steghide’s interface sports no less than 16 different encryption algorithms (Arcfour, Blowfish, Cast-128, Cast-256, DES, Enigma, Gost, Loki97, Rc2, AES 256/128/192, Saferplus, Serpent, TripleDES, Twofish, Wake and Xtea), and for each of them you can define a mode of operation (OFB, CBC, CFB, CTR, ECB, NCFB or NOFB). The default one is Rijndael 128.
Size of the resulting file can be maintained between accepted parameters by defining the compression level. This will have an influence on the total embedding and extracting process, but the resulting file will be smaller, thus easier to transfer.
On the downside, when attaching a secret to the cover file you cannot store the output result in a location of your choice; you are forced to use the cover file’s original location. Otherwise you risk the entire file hiding operation.
Steghide UI features the possibility not to use the cover file and define your own name for the resulting item, but during our tests it would produce a file with no extension which could not be squeezed of the attached content.
Another problem we bumped into while tinkering with the application is regards the type of the secret data. We encountered no problems attaching documents and text files, but we were unable to hide MSI or EXE data. We had trouble using WAV files as containers as in some cases the application would not attach the secret files to them and instead would create a stackdump file showing that there was a problem on the way.
The drawbacks do not stop at this, as extracting the secret attachments and defining the output file name yourself leads to a file without extension, just like in the case of embedding. However, everything is okay if you add the extension of the original file yourself.
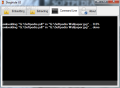
Even if in most cases the purpose of the interface is to hide the command-line tool and make the entire program user-friendly, Steghide UI does not eliminate the possibility to handle the application from the command line. The original help file which provides all the commands is included in the package so that computer savvy users can handle the program the way it was originally intended to.
Steghide UI is just the cosmetic part of the program and we found it to be extremely handy for the average user. The flaws we encountered belonged to the program itself and need to be corrected by the original author.
The frontend is simple and to the point, but it can be further improved, at least by adding a progress bar so the users can see the current state of the job without having to move to Command Line tab. Also, in case of errors, we expected to see a clear sign instead of having to deduce from the creation of the stackdump file.
As far as the command-line tool is concerned, the set of encryption algorithms is truly impressive. There is no progress bar to show you an estimate for completing the running task. Also, we could not set a different name for the output file when embedding as the result would be an item without extension.
The Good
The Bad
The Truth
 14 DAY TRIAL //
14 DAY TRIAL //