As Odysseus was searching for a way into Troy he found out that it was not possible to enter by force, and a stealthy method had to be developed: he ordered that a wooden horse statue were built and delivered to Troy; the catch with this statue is that it was hollow and could have Greek soldiers hidden within it; the Trojans (people that lived in Troy) were fooled into trusting that this was safe, but little did they know that at night, when they were all asleep, the soldiers would get out of the statue and commit a great massacre.
This is a sinister legend, but it has set the basis for a threat that menaces our computers: Trojans. These are small applications that fool you into believing that they're safe to download, install and use, when, in fact, they're sole purpose is to damage your system.
While real viruses can replicate themselves by destroying the host cells, software viruses do the same thing just that they destroy the host computer. Trojans are not able to replicate themselves, but their effect can be catastrophic: they can retrieve personal information such as usernames and passwords, and send it to the "developer".
Attack the attackers!
It's time to call in the Special Forces to take care of this menace, and TrojanHunter is an application that will do this for you. It's only specialized in finding and removing Trojan threats on your computer, and is not a complete antivirus solution.
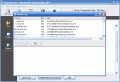
When running the program you'll see a friendly interface, which allows you to scan your computer for threats in a single click. Since its competence area is restricted to Trojans alone, you won't expect to see that many features and options.
The work area takes up most of the window, and you have three different views of it, depending on the section that you select. So, if you're in the Scan section, the work area will consist of a folder explorer that allows you to select which directories you want to include in your scans. Of course, it's recommended that you scan the entire hard disk, but if you've recently been surfing the web, and want to scan the downloaded files, you won't have to go through the trouble of scanning the entire drive.
The Trojans section provides a wide list of threats that you have to be protected against. Each of them has a short description, so that you are well informed on the potential danger. This feature is useful when you're performing a system scan, and the program finds Trojans that you don't know anything about.
The threat list must be updated periodically, and the program allows you to do so, by selecting either the USA, or the European Mischel Internet Security server. This will not only update the list, but will also enable the program to "cure" your computer if a new Trojan has infected it.
The program is even more useful for scanning individual files, since it's integrated in the Windows Shell, allowing you to select any file or folder, and scan it as you browse through the operating system, without having to enter the program.
Also, in order to prove TrojanHunter's strength, you're able to use command line parameters, so that a DOS scan can be performed.
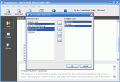
You can perform three types of scanning operations: full scan, quick scan and custom scan. While the full scan takes care of all your hard drive, the quick scan only checks the essential directories; you're able to combine both of these in the custom scan section, by selecting which folders you would like to have cleaned out.
But a scan from time to time isn't enough, and since Trojans now have the possibility of infecting your computer via ActiveX components, and other such small programs, you need to be constantly protected. The TrojanHunter Guard does just this - scans files and folders in the background, and monitors your activity so that no dangers might threaten you.
The program is also able to scan Zip files, Rar files and binded executables, since Trojans could easily hide in any of these components.
If you suspect that your computer might be at risk, you can use one of the five built-in tools to identify the source: Process Viewer (similar to the process section of the Windows Task Manager, allowing you to terminate or get a detailed view of the processes that are running on your system), MemString (which shows you the processes along with the PID and path), AutoStart Explorer, which lets you know what applications automatically launch themselves when Windows Starts, Netstat Viewer (which provides information about the network activity), and the Window list (this component shows you the windows that are created after installing applications on your computer; it includes the class name and title, as well as an icon that shows whether the window is currently hidden or visible.
You can also choose from a set of built-in plugins, that allow you to perform one of the following scans: Registry checker, INI file checker, file checker, advanced file checker, port checker, process checker, script checker, generic checker, application start method checker, shell executable checker, Win.ini startup entry checker, LSP checker, and Extension checker.
The Good
It's easy to work with the program, and the features that it comes with allow it to do a great job in eliminating any Trojan threat. It has a nice and compact interface, so you won't get confused when working with it.
The Bad
This is only a 30 days trial, and if you want to buy the full license, you'll have to pay $49 to get it; for this price you can find a full antivirus solution, but the Trojan protection is worth every cent.
The Truth
The price isn't the best on the market, but the TrojanHunter is good. You should at least give the trial version a try and see whether you want to switch to the full version or not.
Check out the screenshots below to get a glance at the program in action:
Installing:
Working with the program: 14 DAY TRIAL //
14 DAY TRIAL //