protect a Windows Internet server, complete information and control over network security #Port Scan Detection #Remote Administration #Block IP address #Firewall #Detect #Remote
8Signs Firewall software has been designed for administrators wanting to protect a Windows Internet server, and power users who want complete information and control over their network security.
Here are some key features of "8Signs Firewall":
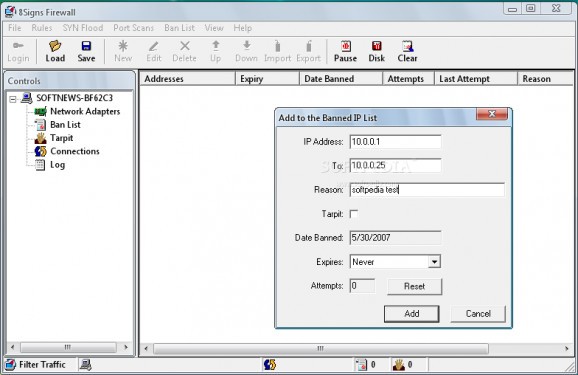
Stateful Packet Inspection �■ 8Signs Firewall uses stateful packet inspection to help detect malicious traffic and ensure that only correct data is passed. Every packet in a connection is checked to see if it is valid. TCP header flags, sequence numbers and other packet contents are used to monitor the "state" of the connection and any packet that does not conform is blocked. This allows 8Signs Firewall to catch malicious activity such as port scans, certain DoS (denial of service) attacks and fragment attacks. Port Scan Detection �■ Port scanning is one of the most fundamental techniques that a hacker may use to begin an attack. An attacker can potentially discover a wide variety of information by performing a scan, such as services you are running, what versions of those services you are running, and even what operating system the host uses. In many cases, information revealed during a port scan can leave a system highly vulnerable to an attacker. �■ 8Signs Firewall detects the seven most common forms of port scans, alerting you with a log entry and optionally automatically banning the IP address of the scanner, ensuring that they are "cut off" before they can discover any useful information about your system. Ban List �■ 8Signs Firewall lets you block IP addresses or ranges of addresses to prevent unwanted connection attempts. This can be particularly effective in stopping repeated requests from a hacker who is trying a large number of hacks, looking for one that works. Entries to the Ban List can be made manually, or automatically using the "Ban IP" action on a Block rule, the Port Scan feature or the by using HTTP Filtering option. �■ To help link other programs (email, IDS, etc.) to the firewall for banning IPs, ban list entries can also be added or removed from the command line. Tarpits �■ 8Signs Firewall allow you to trap hackers, slow down the spread of worms and stall spammers by creating tarpits. A tarpit is a trap for troublesome outsiders. Your system accepts TCP connections but never replies and ignores disconnect requests. This can leave ports scanners and hackers stuck for hours, even days. Remote Administration �■ Using the remote administration component of the Server version of 8Signs Firewall, you can now remotely administer any 8Signs Firewall using an encrypted communications link. Remote systems are controlled through the firewall interface, just as you access the firewall on your local machine. You can monitor activity and log messages, and rules can be added, edited, deleted, imported or exported. You can also reboot or shut down the remote system using the remote admin controls. �■ In addition to remotely administering other Server or Workstation firewalls, you can use the stand-alone Remote Administration Tool to remotely connect to your own Server firewall. HTTP Filtering (Server version only) �■ Using 8Signs Firewall’s HTTP Filtering (available in the Server version only), you can prevent intrusion attempts targeted at your web server by screening requests and automatically banning the offender’s IP address, preventing further access. While HTTP filtering will work to protect all web servers, it has been tailored for IIS servers and the hack attempts that have been targeted at them. SYN Flood Detection and Protection �■ A SYN Flood is a common type of denial of service (DoS) attack used against servers. When launching a SYN Flood, an attacker bombards you with so many connection requests that your computer is unable to accept legitimate connections, effectively shutting down your web, email, FTP or VPN server. 8Signs Firewall employs SYN cookies to protect you from SYN Flood attacks. SYN cookies are a method of managing TCP connection attempts without using up any resources during the process. Since the goal of a SYN flood is to force a server to use up its resources so legitimate users cannot connect, using SYN cookies makes a server much more resistant to this form of attack. SYN cookies are in use in Linux and Free BSD to protect against SYN floods. Port, IP and MAC Address Groups �■ Simplify your ruleset and tighten security by using the port, IP and MAC address groups available in 8Signs Firewall. Using groups, you can create one rule that can apply to multiple ports, IP addresses or MAC addresses. Fine-Grained Access Control �■ 8Signs Firewall gives the administrator unparalleled control over the traffic passing through the firewall. All traffic is blocked by the firewall, unless you have specifically configured a rule to allow it. Rules are configured per-device, and you have full control over the local and remote IP address, local and remote port(s), protocol, and direction of the traffic that you will allow through the firewall. Separate Rulesets for Each Network Adapter �■ 8Signs Firewall allows you to maintain a separate set of rules to be applied to each network adapter in your system. Thus you can configure a set of rules to be applied to traffic passing over your external/Internet interface, while having a separate set of rules that apply to traffic through your internal/LAN interface. MAC Address Filtering �■ 8Signs Firewall now has the ability to filter traffic based on MAC addresses. Because a MAC address is specific to one individual network interface, this feature is particularly useful if you want to allow or block traffic from a particular computer whose IP address may change. MAC address rules can be used to "trust" a MAC address (or group of MAC addresses). This allows you to create firewall rules that will only apply to computers whose MAC addresses are trusted. IP Tracer Tool �■ 8Signs Firewall’s IP Tracer is a tool that will perform "whois" and "reverse DNS" lookups on IP addresses that appear in your log file. IP Tracer can give you information on the source of suspected intrusion attempts, as well as help you troubleshoot any problems that you encounter with applications that are being blocked by the firewall. Easy Importing/Exporting of Rules �■ Deploying 8Signs Firewall across a number of workstations or servers is simplified by your ability to Export and Import rules. These rule subsets can even be shared amongst 8Signs Firewalls running on different operating systems. Full-Time Security �■ In addition to securing your computer while running, 8Signs Firewall is also protecting your system during the boot process. 8Signs Firewall can also be configured to block all traffic to and from your computer when the firewall is not even running! Comprehensive Logging �■ 8Signs Firewall has full logging capabilities. You have complete control over what to log, how large the log file can become, where to store the logs, and how often to begin a new log file. Automatic Emailing of Log File �■ Keeping an eye on your own or a customer's firewall is made easier with 8Signs Firewall's ability to schedule automatic emailing of the log file to any email address that you specify. Remote Notification of Rule Hits �■ Rules can be configured to trigger an email to be sent to any email address that you specify if the rule is 'hit'. For example, if you want to be notified immediately if a hacker is scanning your firewall for the Back Orifice trojan, simply configure a rule that will specifically block this type of traffic and send an email to you if the rule is hit. Time-Sensitive Rules �■ Rules can be configured to only be active on certain days, or at certain times of the day. For example, you may want to allow web browsing only on weekdays between 9:00 am and 5:00 pm, or allow for remote access to your server only on Tuesday evenings for maintenance............this is easily accomplished using time-sensitive rules. Password Security �■ 8Signs Firewall can require that a user must log into the firewall before having access to any of the firewall administration or logging screens. Using password security prevents an unauthorized user from tampering with, or shutting down, the firewall. Control of All Protocols �■ While many firewalls filter only the IP protocols, ignoring others such as NETBEUI and IPX, 8Signs Firewall intercepts them all and can be configured to allow or block this type of traffic. 8Signs Firewall can also control the less commonly used IP protocols such as GRE, which is required for VPN traffic. Connections Display �■ The Connections Display is a real-time display showing all active connections going through the firewall. For example, with 8Signs Firewall installed on a web server a quick glance at the Connections Display would show the administrator how many visitors are currently at their web site.
Limitations:
�■ 30 days trial
What's new in 8Signs Firewall 3.02:
- Fixed bug that could cause the firewall to crash if the user attempted to sort an IP Address Group
8Signs Firewall 3.02
add to watchlist add to download basket send us an update REPORT- runs on:
- Windows All
- file size:
- 5.4 MB
- filename:
- FwSetup3020.exe
- main category:
- Security
- developer:
- visit homepage
Context Menu Manager
calibre
ShareX
Bitdefender Antivirus Free
IrfanView
4k Video Downloader
Zoom Client
Microsoft Teams
Windows Sandbox Launcher
7-Zip
- Microsoft Teams
- Windows Sandbox Launcher
- 7-Zip
- Context Menu Manager
- calibre
- ShareX
- Bitdefender Antivirus Free
- IrfanView
- 4k Video Downloader
- Zoom Client