Privacy is the most cherished thing when we have to deal with computers. Having a machine filled with "top secret" files and knowing they are safe from prying eyes may in some cases be decisive when it comes to sleeping at night.
The solutions to this problem are multiple and go from the simple protection of your computer account with a password (that is if you like to fool yourself) to the most complicated tasks of encrypting the files. If I were you, I would go with encrypting the data and mounting it as a virtual drive every time I need it. And if the drive encrypting software has protection against deleting the virtual drive then it is just too much of a temptation.
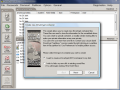
DriveCrypt is a pretty expensive solution for the drive encrypting job, but it has all you need and more. The $59.95 solution for the job at hand comes also as a trial version, but with some limitations (one or more volumes are for demonstration purposes only and insecure). But don't let this stop you from testing as the 30 days evaluation period is enough for you to conduct all your testing.
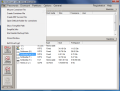
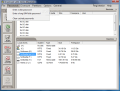
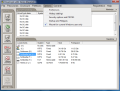
The interface is a bit crowded and the features and options available are abounding. The upper part main area is occupied with the encrypted volumes while the lower is dominated by the real drives on your computer. On the left hand side of the application window, there are the options for managing the protected drives. These are fast ways to mount a disk, dismount it or erase your tracks by clearing the passwords from cache.
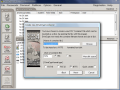
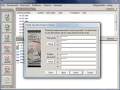
The process is simple, especially due to the wizard that guides you through every step of the operation. First you have to create a virtual disk, which is done in almost no time. All you need to do is give it a name, set its size, choose the format type of the newly created disk, provide a set of passwords (that is right: you can protect it with multiple passwords - up to four of them). In some cases, this would be it.
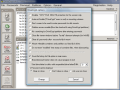
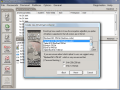
But DriveCrypt takes the job seriously and provides a little more security. Thus, you will have to scramble the data available on it a bit (data is not deleted from the computer, only the names of the files are eliminated, so the info needs a little shake), select the encryption algorithm you want (eleven algorithms to choose from, ranging from 256-bit to the 1344-bit Triple Blowfish), password hashing (SHA 256 with 256bit and SHA 1 with 160bit). That is a lot of complicated work, but it is all for your security. And if you add the fact that clues on options are available side by side with recommendations, it should not take more than two minutes to complete the wizard.
At the end, you will be provided with all the details of the partition and if you agree and don't change your mind or something, then proceed to the volume creation. One piece of advice: when selecting a residence for the virtual drive, make it a DCR container. This way it will be protected against deletion. When you are done with the partition, you can check into Preferences and disable the protection.
This is the first application in its category that I have seen offering this option. Its importance is extreme as there is no use in creating drives that unauthorized persons cannot open if the disk can be deleted without the least opposition from the application.
But creating virtual drives is not all you can do with DriveCrypt. For the ultimate protection, try creating invisible encrypted drives. The operation leads to having an encrypted disk (which is already protected against deletion and by password(s)) which contains another disk. The nice part is that the invisible container is not visible and undetectable and it can also be protected by a password.
The result will be a decoy partition with fake data that incorporates another container with the real data. There are some precautions you have to keep in mind first. You should know that the fake data will take up the space of the real data. That is, if you have an encrypted container 500MB large and place 100MB of bogus data, the invisible partition will be left with 400MB. Also, if fake data increases in size, it will overwrite the information on the invisible container. So you have to be careful at both the amount of free space and the size of the real data on the invisible drive.
Steganograph functions are also present. They will help you disguise the partition and make it look like another type of file than a DriveCrypt container. The container will be hidden in an existent WAV file on the disk. The size of the WAV audio should be of at least 2MB. By this means, you can send files hidden inside an audio file. The size of the newly created partition depends entirely on the size of the audio file. The smaller the audio file, the smaller the container.
Preferences section of the application brings new options for configuring the application. As I've said before, DriveCrypt is equipped with an anti-deleting security measure. The containers created using these files have the extension DCV and they cannot be deleted from the hard disk unless the first option in Preferences is checked (Disable "DCV" File Delete protection).
"Partition access enable" is of special interest as once checked it allows you to encrypt the drives on your computer. Immediately after checking this box in the main screen of the application a new window will appear showing all the available partitions. Simply select one of them and choose from the right click context menu "Reformat Partition As DriveCrypt". A dialog pops up and prompts choosing the format style of the new partition. After that, it is all the same as if creating a new container (virtual drive). DriveCrypt will seal the drive and there will be no authorized access on it.
The Good
Working with the application is not at all complicated and as soon as you get familiar with the interface and the settings, there will be no trouble at all.
Restricting the deletion of the partition containers is simply amazing as it prevents tampering with it in any way.
There are a lot of encryption algorithms to choose from. There is a large pool of options, all aiming to safekeeping your drives, be they virtual or real encrypted ones.
The Bad
Unfortunately, the size of a WAV container is dependent on the size of the audio file. Indeed, taking the real thing and shrinking it is more secure and the container is inconspicuous, but the user will have to deal with limited space.
The Truth
Apart from the "magnificent" price, this is the best I have encountered. It has protection against deletion of the container, invisible disks, real drive encryption, a large pool of encryption algorithms to choose from, steganographic abilities, multiple password protection etc.
The price is the ultimate restriction for buying the software, but it's worth it, since your data will get maximum protection.
Here are some snapshots of the application in action:
 14 DAY TRIAL //
14 DAY TRIAL //