Secure invisible message transmitting software is not too hard to find. It is enough to pick a steganographer and hide your messages into images of different formats. That is one solution, but unfortunately it only gives you the chance to hide the message into a picture file and secure it with a password. The password could be intercepted by unwanted persons and your secret blown.
How about a software that can combine steganography, file encryption, secure deletion, IP-to-IP transfer and locking application? It would be a dream came true if the respective application were also be available at a reasonable price. Well, prepare for all these as Invisible Secrets provides all of the above mentioned at only $39.95. The trial period imposed by the developer is 15 days during which you are free to test a fully functional copy of the software.
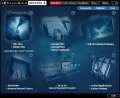
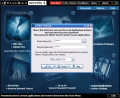
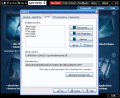
Immediately after launching the application you will be displayed a unique interface that will definitely give you a hint on what it can be used for. Question marks, a lock, a Top Secret label, a shredder, computers protected by passwords and a locked chain are the icons describing the options provided by Invisible Secrets. They are suggestive enough for everybody to catch the idea. If the icons are not enough an extensive tooltip describing the tool is available upon hovering the mouse pointer on the question mark in the upper right corner of the icon.
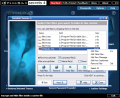
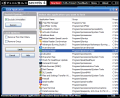
The first tool of the bunch is the steganographer. It is not the usual instrument you may be already be accustomed to as besides the regular "hide-in-picture" option it provides you with the possibility to create fake files. They can be used to divert the attention of possible message interceptors and are randomly generated. The wizard like interface makes it very easy to work with the tool. The carrier can be any JPG, BMP or PNG image, an HTML document or a WAV audio file.
Each of them have certain properties. JPG and PNG image carriers can be placed on a web page, BMP offers the best security, WAV is also very secure and the hidden data depends on the WAV file. HTML is highly secure and does not restrict the length of the sensitive data. However, with all of them care must be taken as too large a file can easily become suspicious and subject to hack attacks.
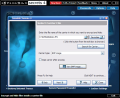
It does not matter the type of files you want to hide in a carrier as long as they are not large enough to create suspicions. The receiver of the file with the hidden message should know the password, and the encryption method (there are eight encryption methods available: AES-Rijndael, Twofish, RC4, Cast128, GOST, Diamond 2, Sapphire II and Blowfish).
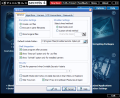
After the hiding of the files is over a new set of options are available for the user. Thus, the resulted carrier can be emailed, or sent to an address through FTP connection. Opening the file to see if there is any visible alteration of the carrier is also possible. If you want to save the hidden message you will have to save it under a different name, as after its incorporation in the carrier it will be wiped. The same is available for the carrier itself if the "Wipe carrier after process" box is checked.
Sending the password to the receiver can also be a problem as it can as well be intercepted. Invisible Secrets has foreseen the mischief and equipped the new version with IP-to-IP tool that is designed to securely transmit the password from one IP to another. The receiver should have a unique global IP and the application installed, open and ready to receive.
Every time a password is being entered, the user has the possibility to type it in by using the virtual keyboard provided. Its advantage resides in the fact that the box where the password is being typed can be masked and the keys can be shuffled.
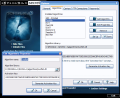
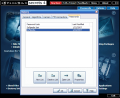
Encrypting the files can be done in a similar wizard like way, only the result will be different. The user can add either single files or entire folders. After the operation is complete the only option waiting is sending the encrypted files to a recipient via email. The original files will not be deleted or modified in any way.
Self Decrypting Packages are definitely my favorite. This type of files does not require any software as they will be compressed into an executable before encryption and decrypting them requires only the password.
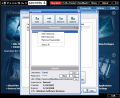
The Shredder has two options available: one for securely deleting any file on your computer or automatically destroy the Internet traces in IE cache or cookies folders, the recently typed URLs, history or MRU documents. The user can use the DoD method for wiping or set up a personal, user defined multi-steps overwrite method. This can be achieved in the Options menu available in the top right corner of the main application window.
Lock Applications feature allows you to encrypt and remove applications from Start Menu. The programs will be protected by a password and this way their accessibility will be much restricted to all the other users. There is a downside of this feature however: if someone gains access to your computer and decides to use a locked program an error message will appear saying that the file is not found or that the shortcut for that application is missing. In this case, that person could easily remove the shortcut from the computer and even uninstall the software with no obstacle whatsoever.
The flexibility the application is also given by the possibilities of adding more carrier extensions and encryption algorithms if you have any. The password manager included in the application allows the user to create collections of passwords and include different countersigns as many as you want. The password manager is also equipped with a very nifty password generator that can create a random countersign just by moving the mouse pointer in a little black and white dotted screen.
The Good
Invisible Secrets 4 can really make invisible all the sensitive data you want to transmit or transfer to a second party. The six tools available combined with the password manager and generator build up for a secure application that can hide and protect all your data.
The Bad
The application locker does not offer protection against uninstalling the locked software. This way you may find yourself installing a program over and over again if someone removes it from your computer.
The Truth
Despite the little baddie for Locked Applications tool Invisible Secrets is a program worthy of your attention. The 15 days fully functional trial gives you a chance to thoroughly testing the program.
Here are some snapshots of the application in action:
 14 DAY TRIAL //
14 DAY TRIAL //