I've recently watched a James Bond movie. It is amazing how many gadgets one MI5 agent can have. Of course many of them are sheer fantasy. I realized that without them he is a simple human being with an above average intelligence. You are probably wondering what came over me to talk about 007.
The software I am going to analyze today is more than worthy to be introduced in the espionage world (between you and me, I think that's where it emerged from). Its name is Steganography and its use is to send hidden messages. Steganography is in fact the art of writing hidden messages in such a way that only the sender and the recipient know about the existence of the message.
You can encrypt any type of file and any type of file you want and send to whoever you want. I know it sounds fantastic, but it is actually true. Do not confuse it with cryptography where the message is not hidden, but obscured. In cryptography you know that what you are looking at is a message, but you have to crack the code.
Let me give you some examples of steganography mentioned by Herodotus. He tells about writing messages on wood boards and covering them with wax (thus it looked like a new, unused writing board). Some more modern techniques involve using invisible ink and writing between the lines (is this where the expression "to read between the lines" came from?).
But with the technology evolving in such a hurry we are the slaves of digital information. And steganography has changed its methods implicitly. Now we can hide messages in MP3s, executable files, pictures, you name it. The technique went so far that it is now possible to insert indistinguishable delays to packets seen over the network from the keyboard. But this is a little too advanced for the average users.
But let's get back to our business. Steganography is a software developed by SecureKit Inc and which was delivered in shareware version to us, having a use restriction period locked to seven days of trial. The full version costs only $24.95.
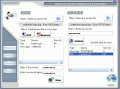
The interface of the software is as simple as can be. You do not need any special skills to use the software, because the hiding of the message or file can be done in no more than three easy to take steps. The software will enable the user to use digital data hiding techniques and encrypt sensitive information by disguising it in a file that will not look suspicious.
The nice looking interface will display a window divided into two antonymous parts: the Hide and the Unhide. The first step you have to take is to choose the "carrier", i.e. the file that will contain the hidden message or file. The carrier can have any form and size and you can choose it to be an executable, a picture, an MP3 file, a video etc.
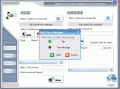
This being done, the next step is choosing the file or message you want to disguise. Press the Add button and make your selection: either a file of any kind or a new message. Press Next to go to the chosen path (if you have selected the File option) or to open the Add Instant Message window. If you just want to write a message, give it a title and proceed to writing it.
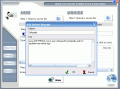
The third step is to specify a password. Thus, even if the message is intercepted, it will also be protected by your password. Click Hide button and the Save As dialog will popup and you can save the file wherever you want on your computer. The hiding is done and all you have to worry about now is not to forget the password and the path to the file that contains the secret message/file.
Unhiding the secret is as easy as hiding it. All you need is the password. The only thing that will cough up the fact that a certain file contains a secret is comparing the intercepted file with the original. The "carrier" will always modify its size. But this can also be tackled by choosing a picture or MP3 file because the size of both of them depends on their digital encryption and the codecs.
The Good
Steganography works just fine and the results are impressive. The three step method will definitely suit your spy features. The job is done fast and the result is secure due to the use of a password for decrypting access.
The best part is that if you choose an executable file as a "carrier" it will install the application and will run as in it does under normal conditions.
The Bad
The shareware version is fully functional for only seven days.
The Truth
The software is extremely useful in the espionage business (I never thought I would say this) and, whether you are a CIA, MI5, NSA, FBI, Mossad, SRI, FSB, FIS or some other secret agent, then this software is a must.
I can now become what every boy wants: a spy. And I will have my own "gadget". The only problem is that there's nobody at the other end to receive my transmissions.
Here are some snapshots of the application in action:
 14 DAY TRIAL //
14 DAY TRIAL //