There is no security suite these days without the all protecting firewall standing at the gates of the computer and watching over every connection, be it inbound or outbound. Being all inclusive when it comes to protection, BitDefender makes no difference and integrates the solution in the package.
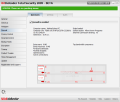
The Summary window provides details on the machine it watches over, such as name, IP and gateway for the Internet connection as well as the amount of data sent and received, ports detected, opened ports, active connections or top bandwidth consumers. Or at least it should because in our case the only information we got was the amount of data sent and received; everything else was there just with the name.
The graphic in the lower part of the status window displays incoming and outgoing traffic. You get the values as well as their graphic representation on a timeframe going from zero seconds to two minutes.
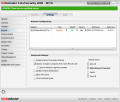
The Settings panel makes available the current network configuration with the network adapter in use, MAC address and gateway used for the Internet connection. Lower in the window you can configure the advanced settings for BitDefender's firewall module and the default action to be taken when a connection is attempted by any program.
You can enable Internet Connection Sharing, wireless notifications or protect yourself against port scans. The module provides four levels of automatic firewall protection, ranging from denying all connections to allowing them with two intermediary degrees, one for reporting any attempt and one for allowing all known programs. I wrongfully assumed that these were the ones included in the rule list as there is no whitelist with BitDefender-agreed software.
It would have been great to have such a list at least for the sake of information if not more. But there isn't such a thing available in the application and you basically have to put your trust in BitDefender. If you set the default action in the Settings panel to "Allow All Known Programs" you will notice that some of the software applications on your computer will have full access to the web while other ones, although with perfectly legitimate intentions, will be denied.
But the more interesting part is yet to come as everyone knows that rules are the heart and brain of a firewall and it is them that dictate how an application should be dealt with. Here you can add any program you deem worthy to be granted free access to the Web and, more importantly, assign it a protocol to use, set the event it should be used for or the direction of the connection (inbound/outbound). Basically, you gain control over how a process connects to or receives packets from the outside and the way the traffic is effected.
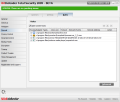
The Rules section presents a list with all the processes BitDefender's firewall has dealt with and the action that has been imposed. Each of the listed rules can be modified to better suit your needs and you have control over the protocols, command line, events and adapter types used.Editing a rule faces you with two tabs, one taking care of the above mentioned settings and an advanced one that goes a bit deeper into the matter letting you select the direction of the connection or the IP version used (this BitDefender has support for Ipv6 as well). Additionally, you are given the possibility to set a local address and port(s) to be involved in the packet transfer as well as a remote location.
If you want to take a look at each process the firewall has dealt with, all you need to do is switch to advanced view of the rules. The window shows the same information as in the Rules panel but every item has its own line and you can move them up and down to suit your needs.
Testing the efficiency of the module was quite a surprise for us as we never expected it to be that firm. The firewall successfully closed all the ports on the computer, thus reducing the risk for uninvited company to sneak in behind our back. But to tell you the truth, I also expected a bit of stealth for the ports, which unfortunately did not occur during our testing. For a more experienced user, having your ports closed basically translates into a bit more effort and does not guarantee failure.
On the upside, few are the users who keep such important data on the computer to tempt a skilled hacker who might want to sneak in. So BitDefender firewall should put up enough protection against the regular nasties. For a home user the security infused by this module should be enough.
Configuring it should take place right from the start, before launching Internet connecting programs, or you will have some tough time reading each alert message initiated by the web activity. Of course, this depends entirely on the default action defined in the Settings panel of the module.
With each message alerting you about this or that software trying to connect to a remote location or receive data from one, BitDefender will also give its opinion on the future action. To tell the truth, during our testing the messages always advised us to allow the connection and we never saw a proposal against it.
We also faced the application against a simple test that involved making explorer.exe and another application call Internet Explorer and adding an additional layer by using svchost via a scheduled task. In the first case, BitDefender's firewall failed to block the action and IE started with no obstacle in its way. At the second test, the application moved a bit slow and failed to alert me in due time about the scheduled task. Actually, I received the message stating the scheduled time about a second before BitDefender's pop-up that would let me decide whether to allow the action or block it.
Bottom line is that BitDefender's firewall is created by human mind and it has its own share of flaws. However, it can successfully serve the purpose of keeping a great deal of shady connections and data away from your computer.
The Beginning Antivirus Module Antispam Module Privacy Control Module Parental Control Module Backup and Restore Module Encryption, Tuneup and Product Tweaks Final Conclusions
 14 DAY TRIAL //
14 DAY TRIAL //